I was wondering that if my data was intercepted by Tor by an exit node, would they be able to see which VPN server is being used to encrypt the data. I am asking because I planned on making an OpenVPN Server and using it with Tor
1 Answers
No, the exit relay does not know your VPN IP.
It might be helpful to understand how Tor works. A diagram from the EFF explains it well:
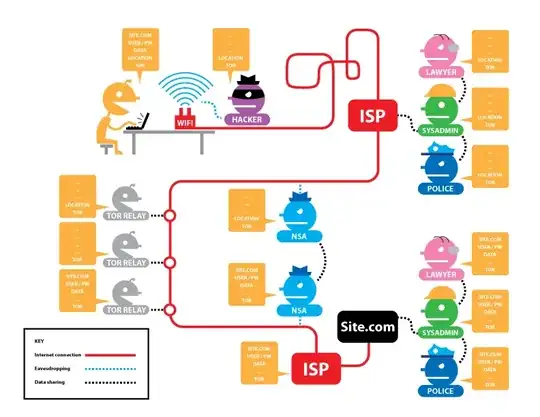
As you can see, the third relay, the exit, can only see the site you are visiting and, if you are not using HTTPS, the traffic to the site itself. The exit does not know your IP. In fact, it does not even know the IP of the first relay (the guard) that you are connecting to. Tor works because no one relay can simultaneously know both who you are, and who you are connecting to. When you use a VPN before Tor, what you are doing is effectively changing your public IP from that of your ISP to that of your VPN. An exit relay whose traffic has been intercepted will not be able to know your VPN IP any more than it would be able to know your public IP were you not using a VPN.
It is important to remember that most of the times Tor has failed people were a result of either operational mistakes or browser exploits. While Tor is very good at hiding the origin of internet traffic, a vulnerability in the browser could be utilized to bypass Tor, revealing your VPN IP or even your real IP. The best way to avoid browser exploits is to keep Tor Browser up to date, and to set the security slider as high is practical. If you want even further guarantees, use Tails.
- 64,616
- 20
- 206
- 257
-
And the relay which knows who you are cannot cooperate with the relay which knows where you connected to. – Michael Hampton Dec 14 '18 at 14:30