Interesting question! I just so happen to have a browser full of test certs, and a number of test sites to connect to! Let's test this!
(Skip to the bottom for a summary)
Investigation
Testing on Firefox
Firefox loaded with certs, a test site that requires a TLS client cert, Wireshark.
I restarted Firefox to get a clean session. Then I entered the URL of a website that will ask for a TLS client cert, and stopped once I got the "Please choose a certificate" popup. This is the wireshark packet capture up to that point:
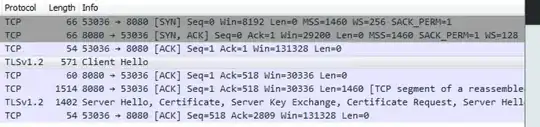
Things to note:
The client sends a generic ClientHello.
The server sends a ServerHello that includes the server cert, and a request for a client cert.
At this point Firefox presents the popup for me to select which cert I wish to send. If I hit Cancel, then there is no further network traffic, ie nothing is sent to the server beyond the generic ClientHello which contains no personally identifiable information. (apart from the list of supported cipher suites, which could be used to determine which version of which browser you're using)
Note1: I tried the same test with only one client cert in my browser, and I even clicked "Remember this decision" on the cert selection popup, and get the same result. So I am unable to reproduce your result of private data being sent to the server without me clicking "OK".
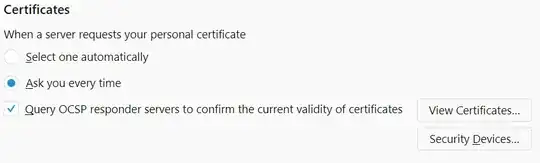
Note2: As pointed out by @JohnWu in comments, you can change Firefox's behaviour in settings in which case it behaves in the same insecure way as Chrome below. Default setting is:
Testing on Chrome
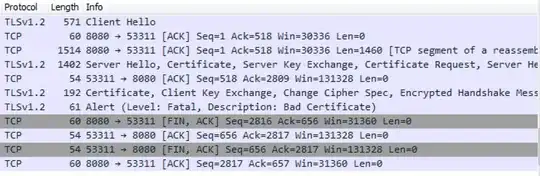
Exactly the same test scenario as above, but with Chrome. (Note that Chrome does not have its own cert store, but instead uses your Windows cert store, which is a bit trickier to manipulate than Firefox. Details for that not included here.)
BINGO!! Chrome immediately starts sending client certs up to the server without any user prompts. This cert got rejected by the server because that cert was for a different website. Yup, that's a privacy concern alright.
Note1: @JohnWu points out that it's possible to change this behaviour and have Chrome prompt, but it's not the default behaviour, and you have to go diving in Windows group policy (GPO) to do it.
Note2: the reproducibility of this may depend on how your Windows OS was configured since Chrome tends to inherit a lot of its security settings from IE.
Summary
In my testing with the two browsers that I have in my test environment (Firefox and Chrome), Chrome exhibited the behaviour you describe (spamming client certs at the server regardless of whether they are from a different site), while Firefox politely asked me to confirm which cert to send, even when I only had one cert installed.
Conclusion: If you care about privacy, then Chrome is not your friend. Use Firefox instead.


