I came across the cybersecurity company Zerodium. They offer bigger bounties than most of the companies calling for bug hunters:
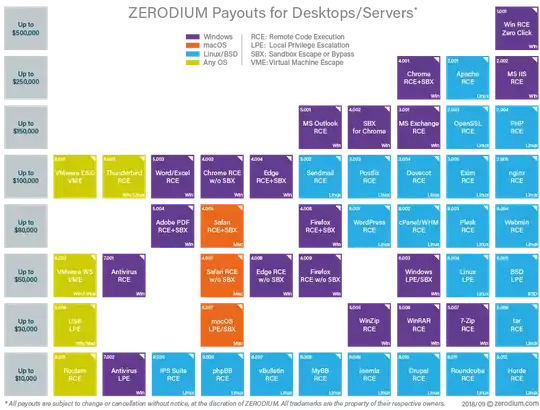
Because of the bigger bug bounties, bug hunters sell their found exploits/bugs to Zerodium rather than to the company having the exploits/bugs.
On their "About us" page they don't mention what they do with their bought exploits and bugs or how they earn their money. In their faq they mention:
ZERODIUM customers are mainly government organizations in need of specific and tailored cybersecurity capabilities, as well as major corporations from defense, technology, and financial sectors, in need of protective solutions to defend against zero-day attacks. Access to ZERODIUM solutions and capabilities is highly restricted and is only available to a very limited number of organizations.
Is there any further information to their customers and what Zerodium does with their purchased exploits and bugs?