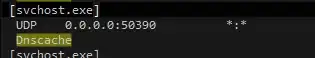
Whats the meaning of "Dnscache" in netstat result?
Its a legitimate client process used as a local store (cache) for DNS responses. All responses are kept for the duration of their TTL.
why it doesn't stop after ipconfig /flushdns
Not sure its suppose to stop/restart/etc. You can run the following command to see if flushdns worked.
ipconfig /flushdns && ipconfig /displaydns
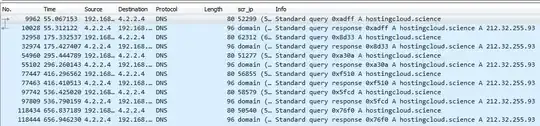
Why client query that domain continuously but i don't have any traffic with the domain?
Dig into the DNS request/response. Perhaps the necessary information is included in that exchange (i.e. DNS data exfiltration).
How to find the root cause?
Take a closer look at the svchost instance. Once you have the PID replace 0000 in the following commands. Compare these results to a known good system.
The following command will list the services using the target svchost. This will greatly narrow things down.
tasklist /svc /FI "pid eq 0000"
The following command will show the loaded modules.
tasklist /m /FI "pid eq 0000"
You're on the right track using procmon. If you're certain that svchost is hosting malware, configure the procmon filter to only capture events for that PID. The resulting information should give you everything you need.
As @razvan-socol mentioned in the comments, use autoruns to identify how it starts up.
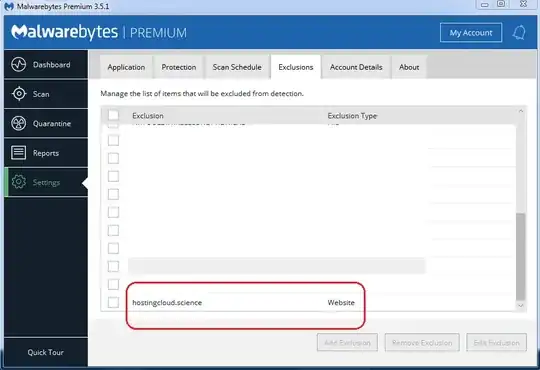
Ps: i checked the client with two different AV and it was clean, Just i know the client has visited a website that contain a js with that domain few days ago.
Its calling out every two minutes though right? And that's not normal for your environment right? With a two minute beacon, the malware doesn't appear to be taking steps to hide its activity. However you should consider taking the system offline for analysis.