Let's threat model using the first two questions of the 4-question threat modeling framework (what are we working on, what can go wrong, what are we going to do about it?) and the threat/requirement/control triangle.
Start by asking what we're working on and what it might look like. You can do this with whiteboard designs. For example, if 'what we're working on' is a new IoT lightbulb which is controlled via the cloud, you can draw those components; if it's controlled by bluetooth, you can imagine what components are there.
From there, you can look at what can go wrong by brainstorming, using STRIDE, or a kill chain. You might list threats like spoofing users at the cloud site, spoofing devices talking to other people's accounts; tampering with the devices at an airbnb, etc.
With that, you can use the threat/requirement/control triangle to use your threats to list requirements. The triangle is:
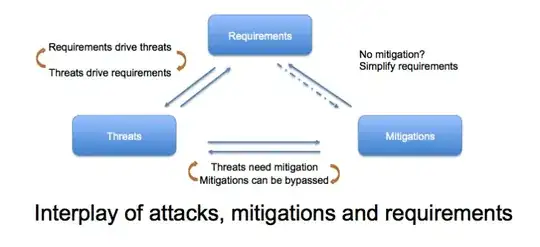
The idea behind it is that you discover a threat, say, anyone can put text on the website. Is integrity a requirement? It's by design that we can edit some, but not all of the text here on SE, and would be a serious violation at whitehouse.gov.
(The diagram is from https://adam.shostack.org/blog/2017/05/threat-modeling-iot/ )
