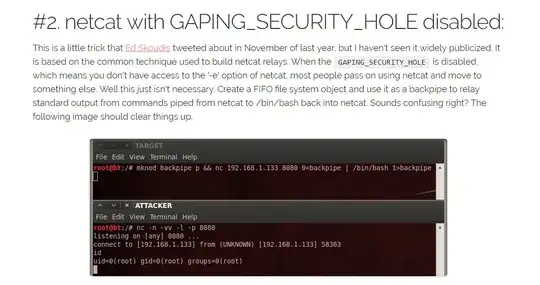
I have been looking at different ways to gain shell access to a Linux machine and came across this article.
Under point #2, there is an slightly different way of using netcat to gain shell. here it is:
According to man pages,
The system call mknod() creates a filesystem node (file, device, special file, or named pipe) named pathname, with attributes specified by mode and dev.
But I still don't understand what is happening and couldn't find an explanation for it online. Can someone please help explain the command in the Target console?
Many thanks!