For the sake of ergonomy, smartphones are equipped with small fingerprint sensors which means they are able to obtain only partial images of a given fingerprint. The chances of a partial fingerprint being incorrectly matched with another "user" fingerprint is relatively high. (cf: MasterPrint: Exploring the Vulnerability of Partial Fingerprint-Based Authentication Systems)
Recently (18 Oct 2018) researchers introduced the concept of DeepMasterPrints which is basically based on training a neural network on a set of real fingerprint images in order to create a synthetic fingerprint able to fool a fingerprint sensor, this is roughly done this way (cf: this paper):
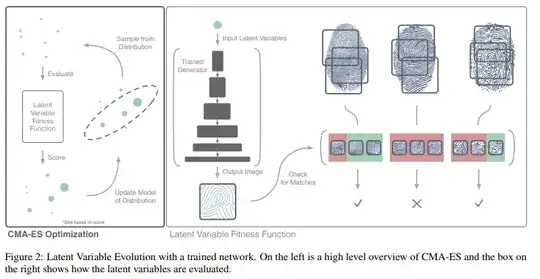
So to answer your question:
This work directly shows how to
execute this exploit and is able to spoof 23% of the subjects
in the dataset at a 0.1% false match rate. At a 1% false match
rate, the generated DeepMasterPrints can spoof 77% of the
subjects in the dataset.
And Google Pixel cannot be an exception.
This said if you're locking your phone to answer a"normal life" need...You do not have to worry :)
