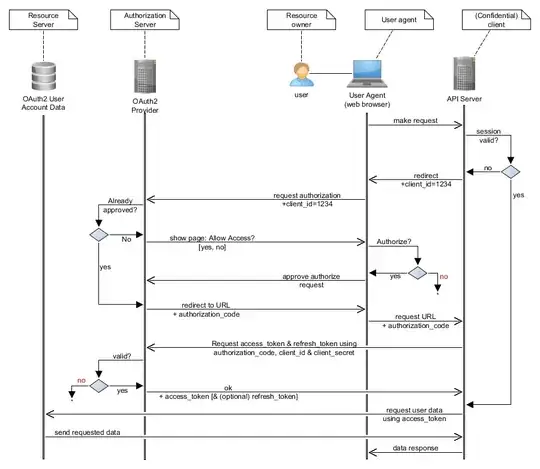
I recently discovered that the applications in our system used plain Oauth2 instead of OpenID Connect to authenticate users. The original use-case was to use OAuth to allow our users to authenticate on the applications using the main application's account, all of which are under our control.
There are a lot of posts around pressing on the fact OAuth is an authorization protocol and as such should not be used for authentication. While I understand the difference between the two notions, I'm having trouble finding information about what actually is the risk of doing so, and what kind of attacks could be made on the system and lead in a user being impersonated.
All I could find were either attacks that weren't specific to the authentication use-case (CSRF during the authorization procedure for example) or implied a malicious client application reusing the user's authorization. But these threats seemed only pertinent when using public services such as Google or Facebook as identity providers. In my use-case, both identity provider and clients are under control, effectively denying the threat of a malicious third-party client.
As such, what are the risks associated with using OAuth to authenticate users when all clients are under control?