In recent black-box pen-test of a webapp hosted on CentOS, I found a vulnerability that allowed me to grab contents of files (kind of file inclusion) located within the home path of Tomcat.
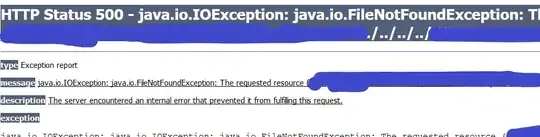
In classic scenario, I tried to read /etc/passwd but failed to retrieve contents. It seems, Apache Tomcat forbids web server from reading outside of web app path. Vulnerable parameter located in GET request and application appends .jsp to that and tries to read it.
For example, if we navigate to http://site.com/abc.jsp?param=en then application will try to load /some/folder/somefile_en.jsp file from filesystem. If it fails, it returns HTTP status code 500 with java.io.IOException stack-trace.
For bypassing .jsp restriction, I added ? at the end of vulnerable parameter like this http://site.com/abc.jsp?param=asdasd_asdasd/../../../../META-INF/MANIFEST.MF?. I was only able to read these files:
/META-INF/context.xml/META-INF/MANIFEST.MF/WEB-INF/web.xml
I do not know what other files I can read (because I do not have fuzz list for java apps).
Q: Could you give me fuzz list for finding other sensitive files in filesystem or could you suggest me other attack vectors?
P.S. I could enumerate file and directory names based on HTTP response. If file does not exist, this kind of error message appears: