Section 164.514(c) of the HIPAA of Privacy rules discusses re-identification of PHI.
If a covered entity or business associate successfully undertook an effort to identify the subject of de-identified information it maintained, the health information now related to a specific individual would again be protected by the Privacy Rule, as it would meet the definition of PHI. Disclosure of a code or other means of record identification designed to enable coded or otherwise de-identified information to be re-identified is also considered a disclosure of PHI.
https://www.hhs.gov/hipaa/for-professionals/privacy/special-topics/de-identification/index.html
Under these rules, what is the possible purpose of de-identifying while retaining a method of re-identifying?
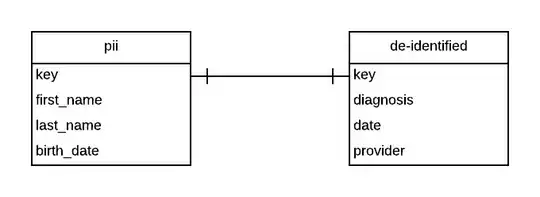
I could imagine someone wanting to store tightly secured HIPAA-protected information separately from less tightly secured non-HIPAA-protected information.
But the except says that the linking key is itself considered PHI. So the de-identified information (including its key) is no less HIPAA-protected PHI than the the original data.
Am I misunderstanding the security requirements here? It seems pointless to de-identifying while retaining the ability re-identifying since both data sets are treated as PHI anyway?