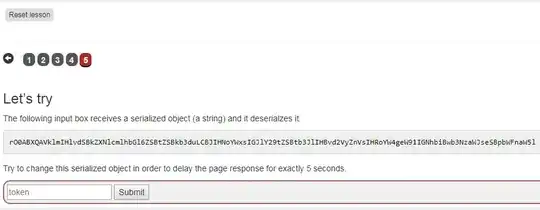
Working on the Deserialization exercise in Webgoat (v. 8)
The Burp extension "Java Deserialization Scanner" detects that this page is potentially vulnerable to the Hibernate 5 (sleep) payload.
However, the payload used in the scanner does not satisfy the exercise. ysoserial is the tool that can generate payloads but I was getting errors.
The following article helped Java Deserialization — From Discovery to Reverse Shell on Limited Environments Here is What I tried: compiled latest release of ysoserial with:
mvn clean package -DskipTests -Dhibernate5
generated the base64 encoded payload with:
java -Dhibernate5 -jar ysoserial-0.0.6-SNAPSHOT-all.jar Hibernate1 "Thread.sleep(5000)" | base64 -w0
(also tried "sleep(5000)", "sleep 5000")
This fixed the errors and resulted in a long base64 encoded string that I pasted into the form field (but now with the result that "the solution is not correct").
Has anyone solved this exercise?