These days I see a lot of browser wrappers in software. For example:
- when you purchase something in the Steam desktop application and use PayPal, you enter your PayPal security details in a browser frame provided by Steam.
- when you log in on the Figma Desktop App with Google, you enter your Google credentials in a browser provided by the Figma Desktop App
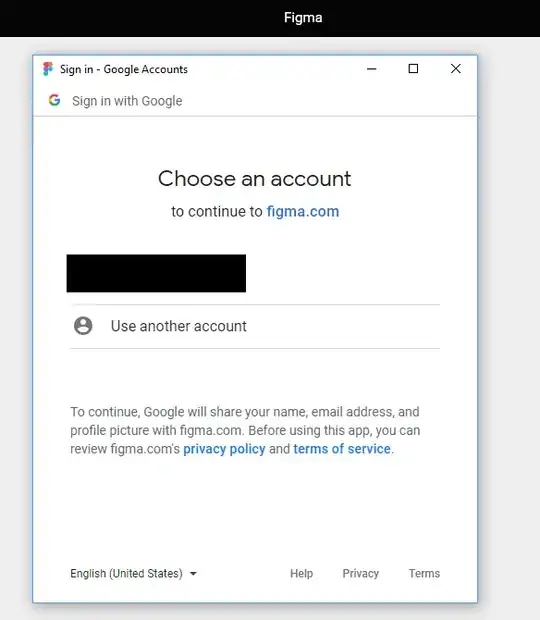
Like trusting my browser, I trust these applications to not mess with the website or frame in any way. For example injecting javascript, showing a phishing page, showing HTTPS when there's no secure connection.
What I'm worried about is users getting used to this kind of presentation. They're exposure to these kinds of browser wrappers might give them the idea that it's OK to trust these kinds of wrappers and freely enter any kind of information there. Not knowing that hijacked or malicious applications could trick users into giving up their details.
Question: am I missing something here or is this a trend that needs to be put to halt? (and instead just serve webpages in the users' preferred web browser)