My family member has reason to believe that someone entered their house last night although they cannot be certain because they only have circumstantial evidence: In the morning they found a light left on and a door leading to the garage left open after locking it last night.
For the sake of this post, let's assume that someone did enter their home without permission.
My sibling owns an AMD PC running Windows 7, and upon waking the computer up today for the first time, this screen appeared:
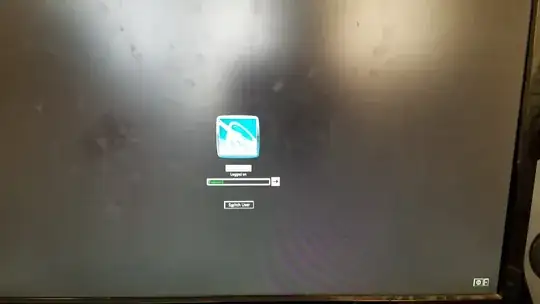
This seems abnormal to me. (The white bar in the picture was added by me and is to hide the user name. Before editing, the font and color of the user name seemed normal.)
After inspecting the computer and seeing no physical changes, my sibling checked the Windows event logs as well as the Windows Administrator logs and didn't see any suspicious events.
My questions are:
- How can we go about verifying that no new software has been installed (Via live cd/usb etc) onto Windows beyond checking logs?
- What measures should we take to make sure that the computer is safe to use?
Some notes:
- Wiping the computer is not a desired option because of personal files.
- We are fairly certain that no physical changes were made to the computer because the internals and rear of the tower were covered in undisturbed dust.
- My sibling is running Windows 7 Home Edition
- BIOS settings show "Removable Device" is set as the first boot option, although this may have been priorly set by me or someone we trust.
I apologize if I've left out any important details, please let me know through comments and I will add them if I can.