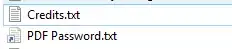
So I downloaded a PDF which is password protected. Inside the same folder there are the following apparently harmless files:
As you can see, they are both .txt files, right? Pretty harmless.. Actually, not: if you look closely you can see that the PDF Password file is actually a shortcut link, investigating within it, it has the following command in the shortcut:
C:\Windows\System32\cmd.exe cmd /c Credits.txt
Ok. So it's not a .txt file and it runs a command for the other apparently harmless .txt file.. which also happens not to be a .txt file, because it's contents look something like:
Binary data. So when you run this, a process called TaskMgr with a weird icon appears. I'm a programmer and I'm curious, what's the anatomy of this attack? What type of data can be run using CMD like this? Which programming language is in this file and how can I decompile it to see exactly what it's doing to the system?
I must admit, this one is pretty clever.