I create desktop client for one e-shop and this client will use some functions using e-shop's API, like:
GetOrders
UpdateOrder
SetOrder
etc...
I'm creating custom authentication for that client, but I don't know is it is secure against attacks.
All communication with client-server is done via HTTPS.
It works like this:
At the first request client have to provide username and password to server. So client will hash that password what user inputs and then client will send request to server with username and hashed password.
Server compares hashed password with hashed password in DB for that username, if it equal then server generates token (like api key) with limited life time and this token will send back to client.
Client will use this token in future requests.
At every successful token request server will renew token lifetime.
Requests should look like this:
POST /orders/get HTTP/1.1
Host: example.com
token=123456789&orderid=10
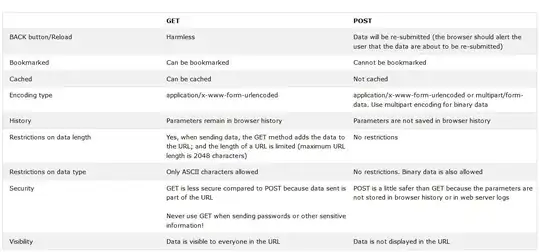
Is there any security recommendation if I should use POST requests or GET requests? Isn't POST more secure then GET? For example POST stores data in body of the HTTP request, but GET it stores in URL.