No, it's generally not possible, as long as all the certificates are generated with proper Extended Key Usage (EKU) X.509 field value and all your TLS servers respect RFC.
For a client certificate, EKU should contain the TLS WebClientAuthentication value, and for a server certificate, should contain the TLS Web Server Authentication value.
(Note that I'm providing human-readable description of the fields and values, not the actual OID values.)
It is common for certificate authorities to include also TLS Web Client Authentication value in a server certificate, which is not bad in and of itself (at least personally I don't see an attack scenario here), but not vice versa.
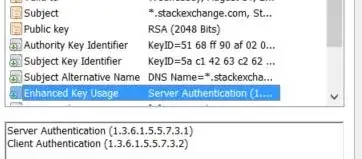
Take StackExchange certificate as an example:
Signature Algorithm: sha256WithRSAEncryption
Issuer: C=US, O=DigiCert Inc, OU=www.digicert.com, CN=DigiCert SHA2 High Assurance Server CA
Validity
Not Before: May 21 00:00:00 2016 GMT
Not After : Aug 14 12:00:00 2019 GMT
Subject: C=US, ST=NY, L=New York, O=Stack Exchange, Inc., CN=*.stackexchange.com
X509v3 extensions:
X509v3 Extended Key Usage:
TLS Web Server Authentication, TLS Web Client Authentication
Also, a server certificate contains the domain name of a server in either the Subject or in the Subject Alternative Name X.509 fields. For StackExchange it looks like this:
Signature Algorithm: sha256WithRSAEncryption
Issuer: C=US, O=DigiCert Inc, OU=www.digicert.com, CN=DigiCert SHA2 High Assurance Server CA
Validity
Not Before: May 21 00:00:00 2016 GMT
Not After : Aug 14 12:00:00 2019 GMT
Subject: C=US, ST=NY, L=New York, O=Stack Exchange, Inc., CN=*.stackexchange.com
X509v3 extensions:
<...>
X509v3 Subject Alternative Name:
DNS:*.stackexchange.com, DNS:stackoverflow.com, <...>
Here, the Common Name in the certificate equals to *.stackexchange.com, and Subject contains the Common Name.
Now, to start issuing client certificates, you usually have to come up with a naming scheme, i.e. what you put in the Subject field and the nested Common Name field. How you do that is completely up to you, but better make sure that under no circumstances could a Common Name within a client certificate coincide with a Common Name of one of your domains, in case either your CA or some of the TLS-enhanced applications in your infrastructure do not obey RFC strictly.
A simple way to ensure this is to put the full name of a user into the Common Name and then make sure that each client certificate issued either does contain a space, or doesn't contain a dot. As far as I know, at least one of those two requirements could be satisfied with pretty much any full name which exists in the world.