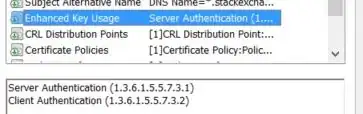
I'm trying to use a service that uses a self-signed cert.
Download the cert:
# printf QUIT | openssl s_client -connect my-server.net:443 -showcerts 2>/dev/null > my-server.net.crtCheck that it's self signed (issuer and subject are the same):
# openssl x509 -subject -issuer -noout -in my-server.net.crt subject=O = Acme Co, CN = Controller Fake Certificate issuer=O = Acme Co, CN = Controller Fake CertificateTry to use it with curl's
--cacertoption:# curl https://my-server.net --cacert my-server.net.crt curl: (60) SSL certificate problem: unable to get local issuer certificate More details here: https://curl.haxx.se/docs/sslcerts.html curl failed to verify the legitimacy of the server and therefore could not establish a secure connection to it. To learn more about this situation and how to fix it, please visit the web page mentioned above.
I don't understand why curl cannot verify the cert.