I live in a country which is under many sanctions. Both internal sanctions (government on people) and external sanctions (US on our people).
In our country, YouTube, Twitter, Facebook and many other sites are blocked by default and we can only access them through VPN.
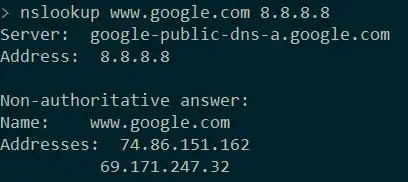
But there is one thing that should work: DNS. If I set my DNS to 8.8.8.8, theoretically it should return the right IP address for www.youtube.com and that IP address should get blocked by the ISP.
But it is not. It looks like our government is manipulating the DNS servers, even the public ones.
I have Ubuntu 18.04 (Bionic Beaver), and I have disabled Network Manager DNS. I have disabled resolvconf and systemd-resolve, by which I mean that no entity in my own system can change the file /etc/resolv.conf.
I changed the content of /etc/resolv.conf to:
nameserver 8.8.8.8
and only this name server. So now every application uses this server by default, and they should query this server for the IP address of websites, but unfortunately they are not doing so!
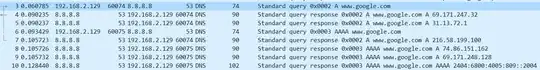
kasra@ubuntu:~$ nslookup google.com
Server: 8.8.8.8
Address: 8.8.8.8#53
Non-authoritative answer:
Name: google.com
Address: 216.58.214.110
Name: google.com
Address: 2a00:1450:4001:812::200e
kasra@ubuntu:~$ nslookup youtube.com
Server: 8.8.8.8
Address: 8.8.8.8#53
Non-authoritative answer:
Name: youtube.com
Address: 10.10.34.35
Name: youtube.com
Address: 10.10.34.35
kasra@ubuntu:~$ nslookup twitter.com
Server: 8.8.8.8
Address: 8.8.8.8#53
Non-authoritative answer:
Name: twitter.com
Address: 10.10.34.35
Name: twitter.com
Address: 10.10.34.35
kasra@ubuntu:~$ █
10.10.34.35 is the intranet IP address for the filtering authority.
How is the ISP achieving this? Are they really stealing and MITM-ing the traffic of 8.8.8.8? Is it some kind of BGP hijack?
How can I get around this without a VPN?