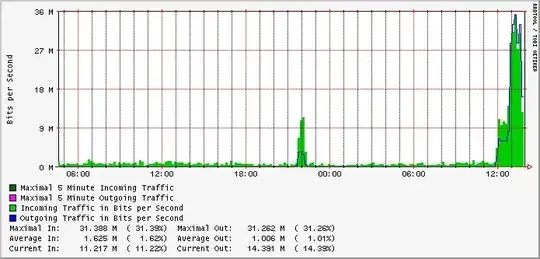
It may not be practical to mitigate DoS attacks just by limiting number of connections, though it could be one of the control. But there are enough technologies available to detect DoS - behavioral, signature based, Pattern based, etc.
You may have to understand the types of possible DoS attacks to plan your Controls/Mitigation Technologies. The context of selecting correct control is based on the asset you are going to protect and potential threats based on the possible vulnerabilities/probabilities.
Possible DoS Attack Types:
DNS Amplification – In a reflection type of attack, a perpetrator starts with small queries that use the spoofed IP address of the intended victim. Exploiting vulnerabilities on publicly-accessible domain name system (DNS) servers, the responses inflate into much larger UDP packet payloads and overwhelm the targeted servers.
UDP Flood – In this attack, the perpetrator uses UDP datagram–containing IP packets to deluge random ports on a target network. The victimized system attempts to match each datagram with an application but fails. The system soon becomes overwhelmed as it tries to handle the UDP packet reply volume.
DNS Flood – Similar to a UDP flood, this attack involves perpetrators using mass amounts of UDP packets to exhaust server side resources. Here, however, the target is DNS servers and their cache mechanisms, with the goal being to prevent the redirection of legitimate incoming requests to DNS zone resources.
HTTP Flood – This attack uses an extremely large number of HTTP GET or POST requests—seemingly legitimate—to target an application or web server. These requests are often crafted to avoid detection with the perpetrator having gained useful information regarding a target prior to the attack.
IP Fragmentation Attack – This attack involves perpetrators exploiting an IP datagram’s maximum transmission unit (MTU) to overload a system. This can be done by sending bogus ICMP and UDP packets that exceed the network MTU to the point where resources expend rapidly and the system becomes unavailable during packet reconstruction. Perpetrators can also execute a teardrop attack, which works by preventing TCP/IP packet reconstruction.
NTP Amplification – Internet-connected devices use network time protocol (NTP) servers for clock synchronization. Similar to a DNS amplification assault, here a perpetrator uses a number of NTP servers to overburden a target with user datagram protocol (UDP) traffic.
Ping Flood – Another common flood-type of attack that uses any number of ICMP echo requests, or pings, to overload the victim’s network. For each ping sent, a reciprocal one containing the same number of packets is supposed to be returned. The targeted system attempts to respond to the countless requests, eventually clogging its own network bandwidth.
SNMP Reflection – The simple network management protocol (SNMP) enables sysadmins to configure remotely and pull data from connected network devices. Using a victim’s forged IP address, a perpetrator can blast many SNMP requests to devices, each being expected to reply in turn. The number of attached devices gets dialed upward, with the network ultimately being throttled by the amount of SNMP responses.
SYN Flood – Every TCP session requires a three-way handshake between the two systems involved. Using a SYN flood, an attacker rapidly hits the target with so many connection requests that it cannot keep up, leading to network saturation.
Smurf Attack – Like a ping flood, a smurf attack relies on a large collection of ICMP echo request packets. But the resemblance stops there, as a smurf attack uses an amplification vector to increase their payload potential on broadcast networks. Smurf malware is used to trigger this assault type.
Ping of Death – PoD is a method by which hackers send abnormal or inflated packets (by way of pinging) to freeze, destabilize or crash a targeted system or service. Memory overflow occurs when it tries to reconstruct oversized data packets. Not relegated to ping alone, attackers can use any IP datagram type to launch an attack, including ICMP echo, UDP, IDX, and TCP.
Fork Bomb – This DoS attack originates from inside of a target server. In a Unix-based environment, a fork system call copies an existing “parent” process to a “child” process. Both processes can then tackle simultaneous tasks in the system kernel independent of one another. Using a fork bomb (a.k.a, “rabbit virus”), a perpetrator issues so many recursive forks that the targeted system becomes internally overwhelmed.
Source: https://www.incapsula.com/blog/security-glossary-top-12-ddos-attack-types-need-know.html