I have been working on a code review of a project. The source code is publicly available on Github.
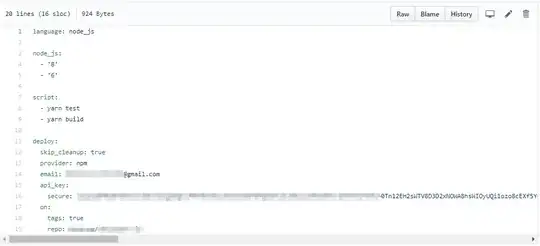
I came across a file "travis.yml". In that file, I am able to see the secure api_key as shown in the screenshot.
I strongly believe that it is a security defect. However, I cannot prove that because I am not sure how an attacker can use that api_key.
Hence please let me know if it is a security defect and necessary justification to prove that. I have blurred few details in the screenshot because of security reasons.