I'm trying to sniff an SSL-encrypted outbound packet. It's sent by the game Mass Effect 3 to an EA web service.
When I sniff packets with Nirsoft SocketSniff, I can see the packet (positively identified by the moment it appears in SocketSniff):
Socket Index Type Local Address Local Port Remote Address Remote Port Send Calls Receive Calls Sent Received Closed
0x00000CBC 24 TCP 192.168.0.111 49191 94.236.58.180 443 5 492 661 1,753 Yes
I can then click on this row to view hex dumps of all communications (in both directions) on the relevant socket. There are 5 sent packets, and 12 received packets, one of which is a partially legible certificate from Electronic Arts inbound to my PC.
I can also see the communication in more detail in Wireshark, which shows this:
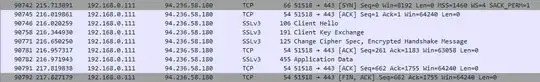 When I click on the Application Data row, I can see hex-dumped ciphertext. However, I want to view the plaintext, so I need to use an HTTPS proxy.
When I click on the Application Data row, I can see hex-dumped ciphertext. However, I want to view the plaintext, so I need to use an HTTPS proxy.
I first tried Charles, which I configured and successfully used to decrypt some HTTPS data to and from a website, as well as some different HTTPS traffic from Mass Effect 3. However, the packet described above does not show up in Charles. I also tried Fiddler 4, which I similarly used to successfully decrypt HTTPS traffic, but the packet does not show up in Fiddler either.
So out of the 4 pieces of software that I used, 2 of them can pick up the packet, but not decrypt it, and 2 of them can decrypt HTTPS traffic, but can't pick up this particular packet.
Any ideas for what I might be doing wrong, or what I can try next? I can provide more information if needed.