I am trying to write a Suricata signature for testing purposes to alert every time it is triggered with a single PCAP file containing a single packet, but this is proving to be harder than I thought.
For instance, I have the following rule.
alert udp $HOME_NET any -> any 53 (msg:"Test A"; \
content:"|01 00 00 01 00 00 00 00 00 00|"; depth:10; offset:2; \
content:"|05|testa|03|com"; fast_pattern; nocase; distance:0; \
classtype:trojan-activity; sid:1099906; rev:1;)
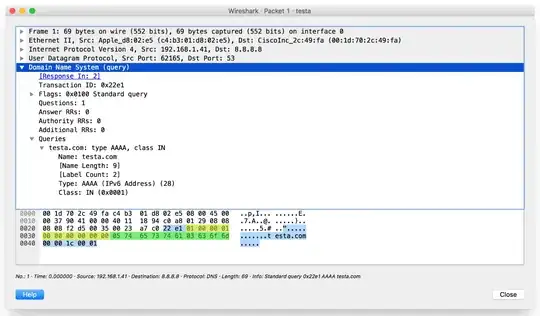
This is a simple UDP signature that looks for the hex 01 00 00 01 00 00 00 00 00 00 defining the UDP packet as a DNS lookup and the domain testa.com.
If I send a pcap with the following content using tcpreplay like this
tcpreplay -i eth0 testa.pcapng
where eth0 is the NIC that Suricata is monitoring and testa.pcapng is the PCAP containing the packet below. I can trigger the alarm once, but if I replay the PCAP, it won't alert until I replay it 3-5 times.
In this image, you can see the matching DNS parameters in yellow and the matching query in green.
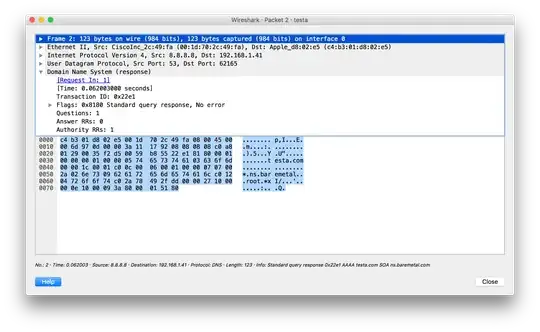
If I add the following DNS response packet to the PCAP:
It seems to fire every time. This is strange, because nothing in the signature looks for a response so how can I write a signature that only needs one packet and fires every time?