There are several questions addressing similar questions, but not quite the same (others ask about MITM Attacks). They also state conflicting and opposing answers/responses, so I ask here 3 specific questions regarding accepting a company’s Wi-fi Certificate when connecting to their network, which is controlled with corporate account credentials to access, on a personal device.
Basically, authentication occurs via company account (email) credentials when selecting the secure network. Once verified, it asks to accept, “Trust” a Certificate as such:
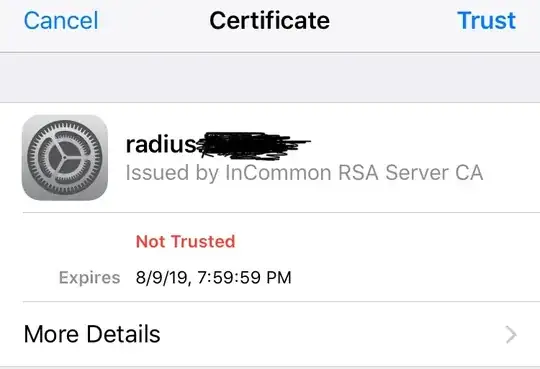 .
.
Looking through the details, I add this to help answer my questions:
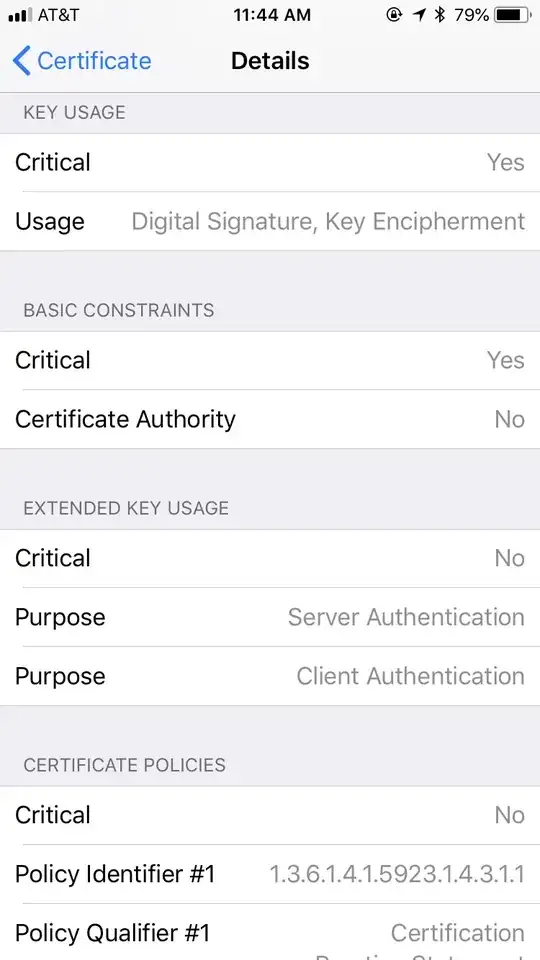
- Does accepting this certificate give the company the right to access my phone? I.e.) does it give some sort of root access or anything like it that allows them to view/access data on my phone. This means accessing both information on the actual device (photos, emails, etc) and data/information being transmitted via the network. I don’t mean monitoring, but being able to access my phone.
- If they can only see/access the data being transmitted through the network (monitoring basically), is this generic like base destination URLs or would it be specific addresses and actual content?
- How would all this be affected by using an independent VPN service? (Someone recommended using it in other questions)
I basically want to know how much right/privacy I would be giving up by accepting to trust this certificate.
For all I can tell is that it may only be for authentication, but is it really only that, and what I’m a further accepting to by authenticating? For all I know, I could be accepting to the company accessing data on my phone.
Thanks in advance!