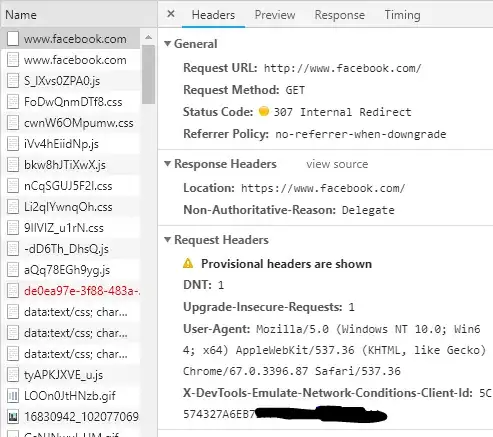
I have several web applications running on my server (Debian 8 running Apache). One of my customers wants to improve the security of his app, after having some security audits carried out by a third-party company he showed me the vulnerabilities he wanted to get fixed, one of these is the missing X-Frame-Options header.
While the header is present in the HTTPS application, it's missing in the HTTP one.
Because of the different requirements of the web application(s) being exposed from the same Apache instance, I cannot define a unique X-Frame-Options header directly in the httpd.conf file.
I've configured an internal redirect http -> https, then adding the www., e.g. webappaddress.com -> www.webappaddress.com.
The problem resides in explicitly asking for HTTP version but not getting the header before the redirection. What happens is: get http version -> redirect on https -> redirect to www.* if missing.
My configuration on the virtualhost (for both 80 and 443):
RewriteEngine On
RewriteCond %{HTTPS} off
RewriteRule (.*) https://%{SERVER_NAME}$1 [R,L]
My configuration on the .htaccess:
<IfModule mod_headers.c>
Header set X-XSS-Protection "1; mode=block"
Header set Strict-Transport-Security "max-age=31536000; includeSubDomains; preload"
Header always append X-Frame-Options SAMEORIGIN
Header set X-Content-Type-Options nosniff
<If "%{HTTP_HOST} != 'www.webappaddress.com'">
Header set Content-Security-Policy "default-src 'self'; style-src 'unsafe-inline' 'self' ;"
Header always set Referrer-Policy "origin-when-cross-origin"
</If>
So my theory is clickjacking could be still possible before the redirect happens (tell me if I'm wrong), but if you look at Facebook or Google they seem to follow the same approach: no security headers before the http->https redirect.