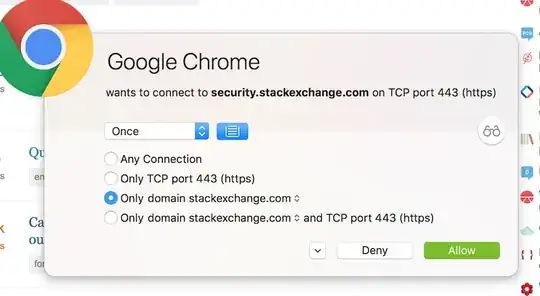
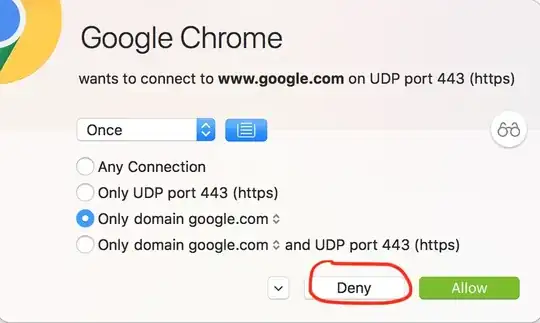
Lawyers. You have a contract with Google stating what they will do / you allow them to do. This is called the Google Chrome Terms of Service . And obviously, you have carefully read it before installing it.
This includes¹ excerpts like this (emphasis by me):
By default, usage statistics and crash reports are sent to Google (…). Usage statistics contain information such as preferences, button clicks, and memory usage. In general, usage statistics do not include web page URLs or personal information, but, if you are signed in to Chrome and syncing your browsing history in your Google Account without a Sync passphrase, then Chrome usage statistics include information about the web pages you visit and your usage of them. For example, we may collect statistics to identify web pages that load slowly. (…) Crash reports contain system information at the time of the crash, and may contain web page URLs or personal information, depending on what was happening at the time the crash report was triggered. We may share aggregated, non-personally identifiable information publicly and with partners — like publishers, advertisers or web developers. You can change whether usage statistics and crash reports are sent to Google at any time. Learn more. If Google Play apps are enabled on your Chromebook and Chrome usage statistics are enabled, then Android diagnostic and usage data is also sent to Google.
Thus, by installing Google Chrome (and not disabling these options), you are granting consent for giving this information to Google.
Would they be technically able to gather more information than what they stated? Yes. Are they purposefully doing it? That's unlikely, as it would place the company in a precarious position should they get caught stealing users data. It is preferable for them to add a note in their policy that covers their gathering (probably including an acceptable rationale like "this will allow us to provide you content more suited to your interests", in an attempt to make it less daunting), as legitimates their practice, and few people read the legal terms, anyway.
Although a story about Google Chrome privacy statements wouldn't be complete without telling how, when Google Chrome launched, its terms of use originally made the user
“give Google a perpetual, irrevocable, worldwide, royalty-free, and non-exclusive license to reproduce, adapt, modify, translate, publish, publicly perform, publicly display and distribute any Content which you submit, post or display on or through” ²
a sentence they were using on other services. After an uproar with this seemingly abusive terms, they updated their terms the next day, stating that for whatever content the user produces using Google Chrome, he retains his rights.
¹ Actually in the Google Chrome Privacy Notice, incorporated by the eula.
² https://www.mattcutts.com/blog/google-chrome-license-agreement/