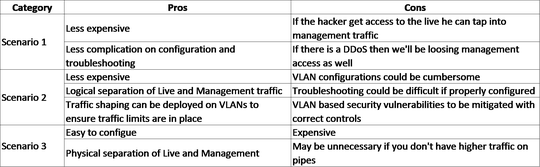What is the benefit of using two network interfaces (management interface and sniffing interface) for an IDS such as Snort? I have used a Snort IDS where it only used one network interface for both management and sniffing and it seemed to work fine with regards to logging alerts on certain traffic.
4 Answers
The main benefit is speed. IDS isnt about prevention but rather about detection, so the packets that are routed to the production machine can be sent directly while the second port can mirror the traffic on the first and send it to a sniffer for the heavy lifting of the analysis. This allows you to split the load between a dedicated production box (or cluster) and a dedicated sniffer/IDS box ... this preventing one from overloading the other.
- 7,517
- 2
- 20
- 40
It is generally recommended that the administration of a security device (IDS, firewall) should be done using a network you can trust as much as possible. One can assume that the network where the IDS is looking for intrusions can not really be considered trusted, otherwise one would probably not use an IDS to detect potential attacks.
The reason why a trusted network is recommended for administrative access is that the administrative access might have its own problems. Several major firewalls already had serious problems that bugs in the administrative access could result in remote code execution with full privileges by an unauthenticated attacker. And one definitely does not want an attacker to be able to disrupt the availability and functionality of a security device or to access sensitive data which the security device can see (for example originally encrypted traffic in case a firewall does SSL interception).
- 184,332
- 29
- 363
- 424
-
if you just wanted to separate out admin from non-admin couldn't you just use one physical ethernet port connected to 2x vlans (making use of Network Alias) – CaffeineAddiction Jun 10 '18 at 20:39
-
@CaffeineAddiction: the OP was asking about different network **interfaces**. I don't understand these as different physical network **cards** (or different physical ports on a single multi-port card) but they could be logical interfaces too, like VLAN. – Steffen Ullrich Jun 10 '18 at 20:49
-
I was just curious if there was a security advantage between physical interfaces vs 2x vlans on the same physical interface ... as far as I know there is not (but could be wrong). – CaffeineAddiction Jun 10 '18 at 20:53
-
2@CaffeineAddiction: VLAN are not equivalent in separation to physical but they come close. Still, for some security requirements this might not be close enough. See also [Why do people tell me not to use VLANs for security?](https://security.stackexchange.com/questions/1551/why-do-people-tell-me-not-to-use-vlans-for-security). – Steffen Ullrich Jun 10 '18 at 20:55
IDS is a listening device not an active device like IPS and following could be the possible deployment scenario (taping on network traffic instead of inline mode):
Scenario 1: Single physical interface – Live traffic and management traffic on same pipe (having separate IPs for separation of communication)
Scenario 2: Single physical interface and 2 separate virtual interface (VLAN) for live and management traffic
Scenario 3: Two physical interface for management and live traffic
There are pros ad cons about all these scenarios and the following table illustrates the pros and cons of each category:
- 2,033
- 1
- 11
- 21
The simplest reason is that IDS is commonly fed via Taps or SPAN ports which do not provide the full RX/TX required for management.
Management of the device requires the ability to both transmit and receive. However, IDS devices are often used to monitor aggregate traffic, and receive their data feed from a Tap or a SPAN port. These ports are, more often than not, RX only. (In fact, back in the day, people used to cut custom Ethernet cables to avoid any chance of their IDS putting traffic on the wire.)
Given this reason - and let's say, for argument, that this specific reason impacted 50% of sites implementing an IDS - it made sense for the industry to split management and monitoring interfaces by default, to make it easier to maintain this sort of separation.
- 71,975
- 17
- 161
- 198