Your question is a pretty good one and as an IAM practitioner I can only apologize for the confusion. IAM is indeed a large field. I think it may be worthwhile taking a step back and going through the basic elements.
Intro
IAM or Identity & Access Management is a field of IT Security (just like network security, crypto, etc...). It can be broken down into four key areas as displayed in the picture below:
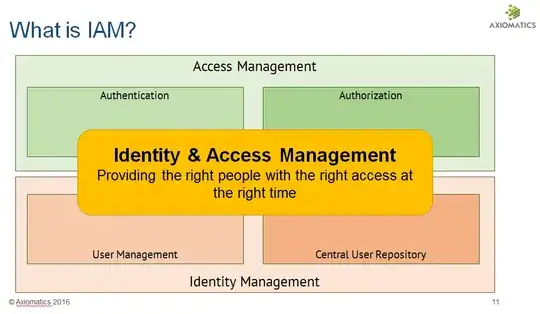
There are several subfields within IAM. Here is a non-exhaustive list
- authentication techniques
- traditional authentication methods
- strong authentication (e.g. one-time password, two-factor auth, ...). Vendors in that space include Yubico.
- Identity Federation.
- Vendors in that space include CA SSO, Ping Identity...
- Identity as as Service (IdaaS)
- Vendors in that space include Okta.
- User management and directories
- user directories e.g. LDAP
- virtual directories. Vendors in that space include Radiant Logic.
- privileged account management (PAM)
- Vendors in that space include CyberArk
- identity and access governance (IAG)
- Vendors in that space include Savyint and Sailpoint
- externalized (dynamic) authorization management (EAM or DAM)
Other areas with relations to IAM
There are side fields that do not belong to IAM per se but definitely help a lot such as SIEM (security information event management). And there are fields that use / leverage IAM such as API security. As a matter of fact, some of the standards you mention (OAuth 2.0, OpenID Connect) are standards that focus on API authentication.
Large vendor suites
You'll find that the larger vendors (Oracle, Microsoft, IBM) all have identity management suites that include some or all of the subfields aforementioned.
Externalized (or Dynamic) Authorization Management
The area I focus on is EAM. In the training courses I give, I typically start with this slide which I hope will help you too:

The de facto model for dynamic authorization management is called Attribute-Based Access Control (ABAC). It's a model that has been around for a long time. It was formalized in 2013 by NIST (National Institute of Standards and Technology).
The de facto standard that implements ABAC is XACML, the eXtensible Access Control Markup Language. It started in 2001 and its current version was released in 2013.
You mention NGAC: that's just an R&D initiative rather than a standard.
Literature in the space
I would refer to Kuppingercole and Gartner as the two main analyst firms that have extensive literature on IAM. They will have good definitions and videos.
Your questions
My main problems are :
Terminology : sometimes, explanations need explanation about the words used
Read through my post, check out Wikipedia, and read the reports by Gartner and the likes.
Different schools of thought : often, there are different ways of interpreting the problems and then even more ways of addressing them. I don't understand what methods are best for what situation, and I want to know why this or that is not as good as another. I see divergent opinions and rarely people set for a best solution or method.
No, in IAM, there aren't different schools of thought. The field is relatively uniform. There are competing vendors and open source solutions but the principles are well set in stone.
Technologies : I've read somewhere that a good access control works in synergy with the filesystem, that should be suited for that purpose. Is that true ? What are these systems ?
This statement is a little odd because IAM is not specific to any one given layer. You should be able to use IAM in any of your layers (apps, databases, filesystems...). Also, the different disciplines in IAM aim to build on interoperable standards so that you can integrate your authentication with your user management with your authorization solution.
References : I fantasise to find a one, "best" reference that would clear all that up, while being objective and addressing things I have forgotten or didn't know.
That's what analyst firms are for. Also consider IDPro, an organization I am a founding member of. We strive to create a space for all IT professionals to take part in, share their knowledge of IAM, or learn more about the space.
For example, I started to think that ABAC would give the best fine-grained control and that XACML, SAML and OAUTH2 used together to form a perfect (yet maybe heavy and complex) system. But then I saw people ranting about it ("yet another OASIS definition") and opposing it to NGAC (Next Generation Access Control).
I am sorry you had to read through this. Let me shed some light.
- ABAC is an authorization model as previously stated. It is formalized by NIST and comes to extend what RBAC has done well since 1992. You can see a quick intro video on RBAC, ABAC, and more here.
- XACML: eXtensible Access Control Markup Language. An OASIS standard to define a policy language, architecture and a request / response scheme to manage ABAC authorization policies.
- SAML: Security Assertion Markup Language. An OASIS standard to address identity federation (amongst other things). It is wildly used for web single-sign-on and federation.
- OAuth 2.0: open standard aiming to fix the "password anti-pattern" whereby a user would have to give service 1 (e.g. Facebook) their password to service 2 (e.g. Twitter) so that service 1 could act on behalf of the user on service 2. With OAuth, you can do that without sharing your password. OAuth 2.0 implements authorization delegation.
- OpenID Connect: a set of standards on top of OAuth 2.0 to address authentication especially in the API world. OIDC has the potential to replace SAML.
How should I operate to gain the right expertise on that subject? In other words: where to start, what to look up next, what to ultimately achieve doing?
This is what this site, Wikipedia, the analyst sites (Gartner and Kuppingercole), specialist systems integrators (e.g. Security Architect in the US), standards bodies (e.g. Kantara, OASIS, IDPro) are for.
I hope this helps.

