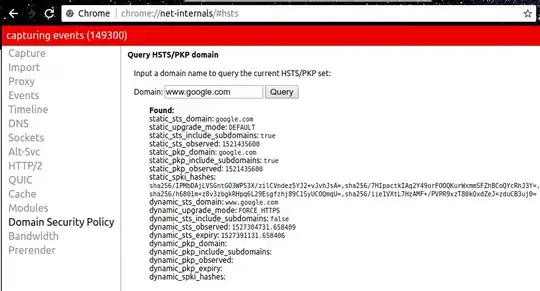
As you may know, you can query chrome's HSTS/PKP sets for a domain in the page chrome://net-internals as below:
As you see above, there are four SHA256 hash values (in the middle of page and in base64 format) for www.google.com.
If we convert those values to hex format, we will have the following values:
ebra@him:~$ echo "iie1VXtL7HzAMF+/PVPR9xzT80kQxdZeJ+zduCB3uj0=" | base64 -d | od -t x1 -w32
0000000 8a 27 b5 55 7b 4b ec 7c c0 30 5f bf 3d 53 d1 f7 1c d3 f3 49 10 c5 d6 5e 27 ec dd b8 20 77 ba 3d
ebra@him:~$ echo "h6801m+z8v3zbgkRHpq6L29Esgfzhj89C1SyUCOQmqU=" | base64 -d | od -t x1 -w32
0000000 87 af 34 d6 6f b3 f2 fd f3 6e 09 11 1e 9a ba 2f 6f 44 b2 07 f3 86 3f 3d 0b 54 b2 50 23 90 9a a5
ebra@him:~$ echo "7HIpactkIAq2Y49orFOOQKurWxmmSFZhBCoQYcRhJ3Y=" | base64 -d | od -t x1 -w32
0000000 ec 72 29 69 cb 64 20 0a b6 63 8f 68 ac 53 8e 40 ab ab 5b 19 a6 48 56 61 04 2a 10 61 c4 61 27 76
ebra@him:~$ echo "IPMbDAjLVSGntGO3WP53X/zilCVndez5YJ2+vJvhJsA=" | base64 -d | od -t x1 -w32
0000000 20 f3 1b 0c 08 cb 55 21 a7 b4 63 b7 58 fe 77 5f fc e2 94 25 67 75 ec f9 60 9d be bc 9b e1 26 c0
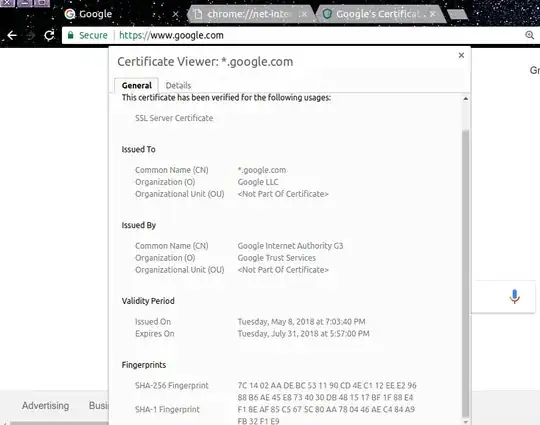
The question is that: why I can't see none of these values in the current loaded Google's certificate in the other tab?