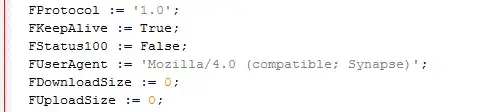
I recently found this request in the event log:
Client IP: 193.203.XX.XX
Port: 53080
User-Agent: Mozilla/4.0 (compatible; Synapse)
ViewState: -1'
Referer:
Now, the ViewState: -1' part combined with the origin of the IP address (Ukraine, we don't have clients there) makes it look suspicious to me. Is this a new kind of attack and should I be worried?
Update
Here's the log:
2012-08-14 10:13:17 GET /Gesloten.aspx - 80 - 193.203.XX.XX Mozilla/4.0+(compatible;+Synapse) 200 0 0 546
2012-08-14 10:13:17 POST /gesloten.aspx - 80 - 193.203.XX.XX Mozilla/4.0+(compatible;+Synapse) 500 0 0 218