We have a WIFI router with SSID: "dummyssid" with our own WPA2 password. Today unexpectedly, another WIFI SSID was available in the WIFI scan list with exactly same as of our SSID: "dummyssid" but without any password. Just at that time internet on our devices, like laptop and mobile phones, stopped working. I suppose because there were exactly same WIFI SSID's in the scan list and our laptop/mobile phone is unable to decide which one to use?
I thought my WIFI router is having some issues. So I disconnected from power it but still that ambiguous SSID was available in WIFI scan list. I tried to connect with that ambiguous SSID, then I tried to access the router web page of that ambiguous WIFI. In that page it asked me for my WIFI password. I didn't entered anything there. Leaving everything as it is. After 30 minutes or so, that ambiguous WIFI is no more visible in list and our internet is working fine again.
This is the page that was showed to me when I accessed router page of that ambiguous WIFI.
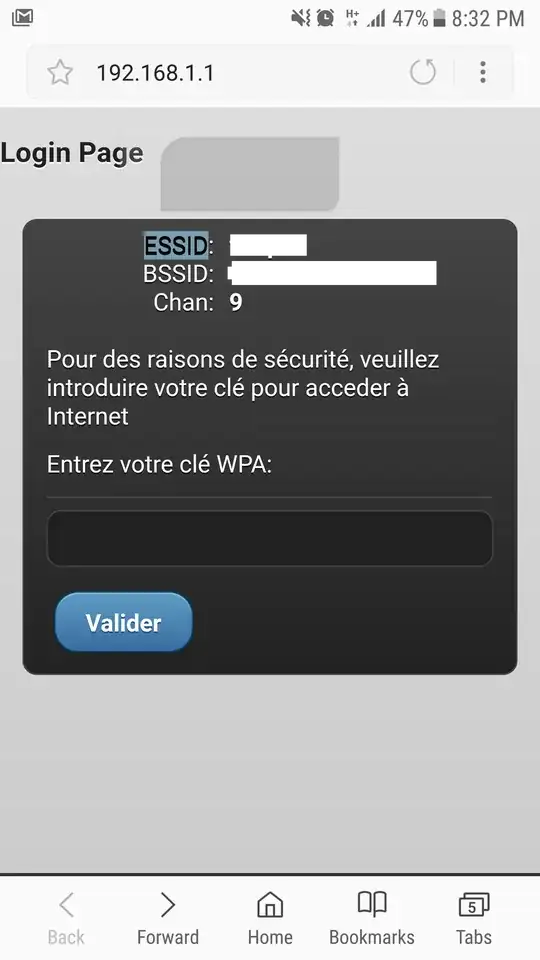
Do you think someone is trying to get our WIFI password by creating an ambiguous WIFI device and pushing us to enter our WIFI password? If that's so, how do you think we can prevent it?