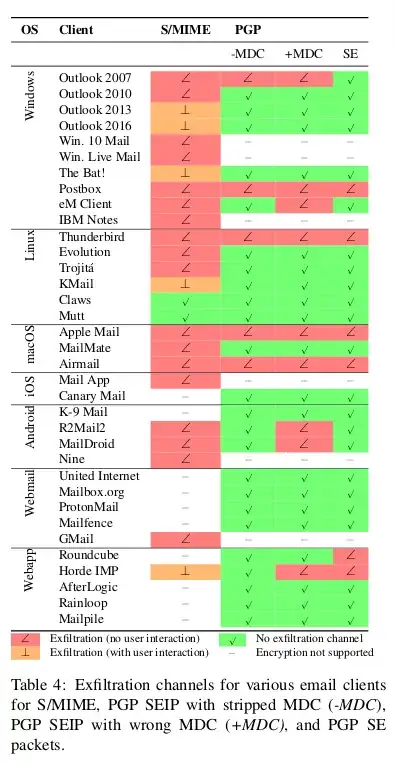
Notably, PGP is not the problem. The problem lies with the mail handling apps in your browser which you have allowed to use your PGP keys. Those browser apps decrypt the message as they should, but inside that message in addition to your secret is a trojan URL which is an attackers site. Your browser app stupidly tried to connect to the URL which has your secret appended at the end.
For most people the most practical method is (from your link):
Short term: Disable HTML rendering. The EFAIL attacks abuse active
content, mostly in the form of HTML images, styles, etc. Disabling the
presentation of incoming HTML emails in your email client will close
the most prominent way of attacking EFAIL. Note that there are other
possible backchannels in email clients which are not related to HTML
but these are more difficult to exploit.
Then any URL in the decrypted message will appear as text, including the trojan URL. Almost certainly would you be able to look at the URL and know something was wrong. If nothing was wrong, and if your mail program has a button to to allow you toggle HTML view for that single mail, you would then be able to safely read the mail.
The other method suggested:
Short term: No decryption in email client. The best way to prevent
EFAIL attacks is to only decrypt S/MIME or PGP emails in a separate
application outside of your email client. Start by removing your
S/MIME and PGP private keys from your email client, then decrypt
incoming encrypted emails by copy & pasting the ciphertext into a
separate application that does the decryption for you. That way, the
email clients cannot open exfiltration channels. This is currently the
safest option with the downside that the process gets more involved.
could be more difficult. On a cell phone it could be very very difficult.
On a laptop or desktop, it depends on how easy it would to set up the non-browser app, or have someone do it for you. The fiddly time spent cutting and pasting depends on how many encrypted messages you have to process.
You would also want to be careful that the non-browser app doesn't automatically try to contact the URL.
EDIT: Adding quotes to message won't protect your sent encrypted mail. Thanks to @Anders for pointing out the reference.