I will be going on vacation for a few weeks to my family home and will be using their wifi for work. The problem is, I am a cam model, and do NOT want them to know that I am visiting the sites let alone broadcasting. I will be using my own laptop, but their internet. There is a MAJOR tech nerd in the house, and I wanted to know if there is a way to block what sites I go to so there is no log of them in the router. Also, could he tell if I am broadcasting video?
-
1Possible duplicate of [If someone hacks my wi-fi password, what can they see and how?](https://security.stackexchange.com/questions/30261/if-someone-hacks-my-wi-fi-password-what-can-they-see-and-how) – AstroDan May 09 '18 at 20:38
-
1@AstroDan I don't think this is a duplicate because this question is specific to OP's scenario. Answers that would be appropriate here (e.g. use a throwaway 3G/4G USB modem for a few weeks) would not be applicable to the other question which is far more general. – forest May 10 '18 at 07:34
-
For people considering marking duplicate, this question is similar in that they would be able to see everything as an attacker with a password, but it is not duplicate as with access to router, they would see more/more easily. His family will not only have password of wifi, but full access to router and any other networking equipment. – Peter Harmann May 10 '18 at 09:19
-
Is this "tech nerd" going to live there with you during this time, or are you the only one living in that house (family is temporarily away)? I wold consider the fact that if the "potential hacker" lives there and meanwhile notices you are using a huge bandwidth, he may want to investigate and even put some hidden cameras in your room. – reed May 10 '18 at 13:19
-
3A good thing to add to your question, how determined/suspicious of you is this tech nerd? One thing is if they just look at traffic, another is if they're determined to know what you're doing and have physical access to your PC. Don't assume threats are only going to come from your network. – BgrWorker May 11 '18 at 10:06
4 Answers
Yes, they will be able to see what you are doing. Firstly, if the website you use does not use HTTPS, they will additionally be able to see any data you are sending, and tamper with it at will. Secondly, they will be able to see the domain you are visiting regardless of encryption status, which itself would likely be pretty incriminating. One solution would be to use a VPN, but be aware that many commercial VPNs can be defeated by a sufficiently tech-savvy attacker. This is because VPNs are designed only to be shared by people who mutually trust each other. Against most people, they are sufficient.
Another thing to be aware of is traffic analysis against videos. This is an issue because video formats are compressed. This causes the raw upload rate to differ over time based on how effectively the given section of video can be compressed. This variable upload rate can be used to identify the fact that a video is being uploaded even if encryption is being used, though in most circumstances it cannot determine what the video is of. There is no effective way to prevent this while doing live video broadcasts if you are on their Wi-Fi. Anyone who looks at the logs will be able to see you uploading a constant variable-rate stream of data. This just screams "streaming live video". Doing this for 6 to 9 hours a day (as you mentioned you do in a comment) may be suspicious to anyone looking at your traffic flow if you don't have another reasonable explanation (e.g. remote meetings).
There is a simple solution, however: don't use their internet! This is easier than it sounds. You can buy a USB 3G/4G/5G dongle which will provide you with high-speed mobile internet (although not enough for HD video). You would likely want to purchase an unlimited data plan if you are uploading a lot. The only way to view this traffic would be to use specialize hardware. This is not likely unless your family is really interested in what you are doing. Chances are, they will not even know you are using a mobile dongle unless you tell them or they actually see it (and know what it is).
Note that not all areas have great bandwidth, and whether or not the upload bandwidth is sufficient depends on how high your video quality needs to be. I've been able to stream video over 4G and was satisfied with the results, but your millage may vary. Test it out before you rely on it.
Although the above should be sufficient for a general answer, you need to formulate a threat model, determining who your adversaries are, what positions they are in, what resources they have, what they are after, and what your assets are. Ask yourself a few questions. You must:
Determine the level of sophistication of your adversaries. Do they merely know the basics of networking? Does their profession involve network analysis? Are they PhD researchers who put out their own novel research related to networking? "Tech-savvy" encompasses many things.
Determine your adversaries' capabilities. Are they only able to access their own router logs? Do they have access to your computer, potentially allowing them to tamper with it? Is there a risk that they will walk in on you doing your cam shows? Might they overhear you outside the door?
Specify your assets. In other words, are you trying to hide the contents of the videos, their destination website, or the fact that you are uploading videos at all? Is it specifically the fact that you are a cam model that you are trying to hide, or exactly what requests you get from clients?
Quantify the threat. Do they not care at all to find out what you do, making accidental exposure the biggest risk? Are they merely curious what you are doing? Are they dead-set on finding out?
Analyze the risks. Would knowledge of the fact that you are a cam model simply be embarrassing? Would it risk you being disowned by your family? Would your very life be at risk?
Here is a hypothetical example of what a basic threat model might look like:
- My adversary is my tech-savvy uncle.
- He is a snoop and doesn't like the idea that anyone is doing something in secret.
- He does incident response for a large ISP, so he knows the tricks of the trade.
- He can only log network activity, not install cameras or tamper with my computer.
- If he finds out what I'm doing, I will be pressured to stop and may lose my source of income.
A threat model will allow you to determine the best way to protect your assets.
- 64,616
- 20
- 206
- 257
-
2Brilliant! I will look into the dongles and see what kind of plan I can get. I need at least 15Mbps upload to keep my stream stable. Any recommendations? – Lindz123 May 10 '18 at 05:43
-
Find any one which is rated for that upload speed which uses a mobile network with coverage where you are at. 4G will of course be faster than 3G. 4G can often give you 50Mbps upload or more. If you worry that there is a change that they will have access to 3G/4G interception hardware (or can build it), then you would want a VPN. The only one I can recommend is Mullvad or IPredator. Setting up your own VPN would be superior, but may not be necessary unless the risks are very high. – forest May 10 '18 at 05:44
-
@Lindz123 Just search for any "4g usb modem" and find one within your price range. Make sure it has coverage where you will be going, and make sure it the upload speed it advertises is fast enough. Customer reviews are useful to make sure it doesn't advertise a higher speed than it actually provides. – forest May 10 '18 at 05:50
-
1"However, be aware that most commercial VPNs can be defeated by a sufficiently tech-savvy attacker. This is because VPNs are designed only to be shared by people who mutually trust each other." Come again? – Daniel B May 15 '18 at 07:59
-
5@DanielB VPNs were designed originally to simply put you behind a NAT that you are not physically on (for example, so you can use your office network and everything on it at home). It is only encrypted so e.g. your ISP cannot see confidential information. The "private" in "virtual private network" refers to RFC 1918 IANA-reserved addresses, not "the right to privacy". Because of this, it is fundamentally designed under the assumption that everyone using it is mutually trusted (after all, it puts them all behind the same NAT). Various companies have exploited the "P" in "VPN" for marketing. – forest May 15 '18 at 08:04
-
4The majority of commercial VPNs are in fact so badly designed that simply signing up to the same VPN as your target will allow you to discover their home IP address, as well as some other juicy info. Even large companies like PIA used to (and might still) have this issue (you'd have to talk to hdm if you want more details on the specific issues with PIA, though). The only solution requires VPN companies do rather complex per-user isolation (completely unrelated to OpenVPN's "user isolation" feature) which is non-intuitive and requires a level of networking expertise. – forest May 15 '18 at 08:06
-
-
1I have to disagree with the recommendation to use 4G data for [15Mbps of streaming video upload](https://security.stackexchange.com/questions/185530/can-my-family-see-what-sites-i-visit-while-i-am-on-their-wifi#comment363601_185554). Two points: 1) High-quality video (15Mbps qualifies) needs much lower delay variation than you get with your typical 4G data connection. My ping times vary wildly sending traffic over 4G modems. 2) Expected throughput over 4G likewise varies wildly. She didn't come back, but I'd wager that the OP was much less than satisfied if she tried this recommendation. – Mike Pennington Jun 21 '18 at 23:55
-
@MikePennington I've had good experience with high-quality video over 4G, fwiw. – forest Jun 22 '18 at 01:38
-
1
-
@MikePennington I don't know if it was 15Mbps, but I was able to stream high-quality videos on 4G. – forest Jun 22 '18 at 01:41
-
14G is fairly asymmetric. Quoting [Verizon's own marketing numbers](https://www.verizonwireless.com/articles/4g-lte-speeds-vs-your-home-network/ "LTE Internet (Installed) provides average download speeds between 5 and 12 Mbps and upload speeds of 2 to 5 Mbps"): *LTE Internet (Installed) provides average download speeds between 5 and 12 Mbps and upload speeds of 2 to 5 Mbps* – Mike Pennington Jun 22 '18 at 01:45
-
@MikePennington According to [this source](https://www.telegraph.co.uk/technology/mobile-phones/11229679/4G-upload-speeds-seven-times-faster-than-3G.html), EE provides 14.7Mbps and O2 provides 13Mbps. As I mentioned to the OP, she has to look at the specific product she is buying to make sure the speeds are acceptable (which would e.g. prohibit Verizon, if its upload speed is as low as you say). – forest Jun 22 '18 at 01:47
-
1In your own source: However, Paul Carter, CEO of engineering company GWS, has slammed the report, claiming that Ofcom’s research does not realistically represent consumers’ mobile experiences. "Consumers who only use their devices while standing stock still in select city centre locations might experience average download speeds of 15.1Mbps on 4G – unfortunately this rules out every real person with a mobile," he said. "This report doesn’t tell us anything about network reliability, coverage, connectivity on the move – it’s the network benchmarking equivalent of a beauty pageant." – Mike Pennington Jun 22 '18 at 01:51
-
@MikePennington Maybe so. Regardless, I have in the past streamed high-quality video over a 4G connection and was satisfied with the result. I do not know if I got an abnormally good connection, or if my opinion of high-quality differs from others. That's just my own anecdote. – forest Jun 22 '18 at 01:53
-
I will say one thing regardless of our disagreement here. I learn a lot by reading your answers about malware and encryption. Respect. – Mike Pennington Jun 22 '18 at 02:36
-
If OP employ and successfully use a DoH agent in his machine, that would make necessarily impossible for anyone in the network to find out which websites are being visited by OP, correct? – Luis Vasconcellos Jan 19 '21 at 17:43
-
@LuisVasconcellos No, because you'd still see SNI being sent in plaintext in the TLS connections. – forest Jan 21 '21 at 02:50
Yes and technically no, but really yes. He can see what pages you visit and he can see you are sending large amounts of data to IP of the web you stream video to. So while he can't really prove you are streaming video (if the stream even uses TLS/other encryption) and not sending something else, it is not hard to figure out. The stream will be recognizable as it is large amount of data going out and it can be distinguished from file upload, because it will be at fairly constant bitrate instead of going as fast as it could.
- 7,728
- 5
- 20
- 28
-
Is there a way to block the site names from my end, or no? I don't care if they see lots of data being transferred, just want to wash the site names somehow so I can keep some semblance of privacy about my job. – Lindz123 May 09 '18 at 20:42
-
1@Lindz123 To hide site names, you can use DNSCrypt. But that is not enough as they would still see IPs, which can be looked up. You will also want a VPN to hide your traffic. https://dnscrypt.info/ Choose pretty much any VPN, dough you may need a fast (paid?) one to stream in good quality. – Peter Harmann May 09 '18 at 20:44
-
Thank you, sir! I will do that. Not sure he would care/be curious enough to go look up IPs, so that will help. Would be nice if there was a simple way to just make it look like I was streaming to twitch or something :) – Lindz123 May 09 '18 at 20:46
-
1@Lindz123 Well, unfortunately there is no way to do that as far as I can tell (without serious serious hacking/equipment). DNSCrypt will hide the domain names and as long as his curiosity is not peaked about them being hidden and he does not look up the IPs because of that, you should be ok. (it is really easy to look them up) – Peter Harmann May 09 '18 at 20:49
-
do you know if a mobile hotspot of my own or jetpack (which i have no idea what that is by the way, but i saw something about it online) would work for streaming live video? That way i would stay off their network all together... Keep in mind that I would be streaming HD video for 6-9 hours a day. Seems like the cost would be super prohibitive if it even worked at all. – Lindz123 May 09 '18 at 20:52
-
@Lindz123 I have no idea what a jetpack is, but using a mobile network would completely bypass the router and their connection in general. As long as you set a strong passphrase for the wifi, you are safe from any normal attacker (someone who does not have stingrays, like a government). But yes, mobile internet would be probably prohibitively expensive. A VPN can cost just a few dollars and would be a bargain in comparison. – Peter Harmann May 09 '18 at 22:10
-
A video would actually involve a variable bitrate (which itself is identifying, since a constant upload rate that doesn't saturate the uplink could indicate uploading to a slow site). – forest May 10 '18 at 06:09
-
@forest depends on encoding but yes. Either way, it would be identifiable. – Peter Harmann May 10 '18 at 09:15
-
-
@forest I honestly don't know. I think we use some on our university, but that is for ridiculous resolutions and more of a research thing. I just did not want to assume they are not used, more general = better IMO. – Peter Harmann May 10 '18 at 09:23
Absolutely. Along with the other answers, don't forget the possibility of an adversary running a custom DNS server.
DNS servers are used to resolve human-readable host-names (such as security.stackexchange.com) to a number that represents the server that hosts the website requested. The default servers a computer will use are generally overridden by the preferred DNS servers of the network. This makes a DNS server used for spying relatively easily implemented, and this server can collect information such as the names of the sites visited. They do not collect webpage data.
It is entirely possible to override the network-provided DNS servers with trusted ones, mitigating the risk of connecting to a custom DNS server.
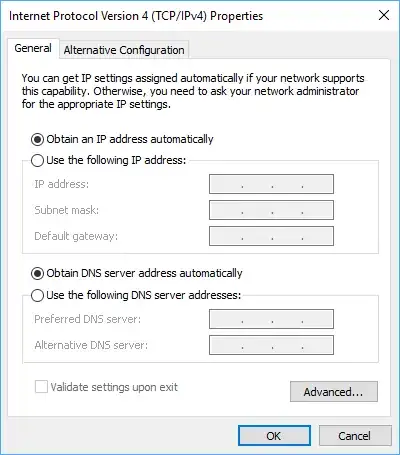
To override the DNS servers in Windows:
- Open 'Start Menu'
- Type 'Control Panel' and press enter
- Click 'Network and Internet'
- Click 'Network and Sharing Center'
- Depending on whether you're connected via Wi-Fi or Ethernet, click on the label that follows 'Connections:'
- An information box will pop-up. Click 'Properties'
- Click 'Internet Protocol Version 4 (TCP/IPv4)' and select 'Properties'. A Popup box like the one below will show up:
- Select 'Use the following DNS server addresses:'
- For 'Preferred DNS server' use 8.8.8.8 (These are Google's public DNS servers)
- For 'Alternative DNS server' use 8.8.4.4
- Do the same for 'Internet Protocol Version 6', using 2001:4860:4860::8888 and 2001:4860:4860::8844 for the DNS servers
This isn't a sure-fire way to prevent snooping but should ensure your web-requests are not handled by anyone in your household. Please do note that traffic snooping and other data-analyzing methods would probably be unaffected by this.
As a side note, I wholeheartedly agree with just using a 3G/4G dongle if your mobile data doesn't cost 'an arm and a leg'
- 11
- 1
-
If the home network admin is knowledgeable enough to run a custom DNS, then the admin will have many, many other technologies in place that would make switching to 8.8.8.8 meaningless. Like logging. The DNS queries to 8.8.8.8 would likely be logged and so would the outgoing traffic, including the URLs. So, I'm not sure this is an effective measure against the threat here. – schroeder May 11 '18 at 09:44
-
@schroeder Some routers can log DNS queries that are made to them (as opposed to ones that pass directly to 8.8.8.8) or do so by default. Most modern routers using DHCP will also tell the clients to connect to the router's own address (say, 192.168.0.1) for DNS. You're right that this is likely not super useful, but you do not need to be tech-savvy to have a router which uses its own DNS. – forest May 12 '18 at 00:33
... And more
There is a known and widely used way to create a In-the-middle SSL Bump proxy. This way will permit same in-the-middle interaction over HTTPS, like over HTTP.
Of course, for making this possible, you have to install and accept one pseudo root CA cert but this could be done without your knowledge by some script that could be
- given on some USB key, as gift,
- installed by wifi router, as special wifi driver,
- injected on you host by using some vulnerability
- and so on...
So definitively YES, using unknown wifi, without strongly secured host could be subject to caution!
- 4,597
- 2
- 19
- 32