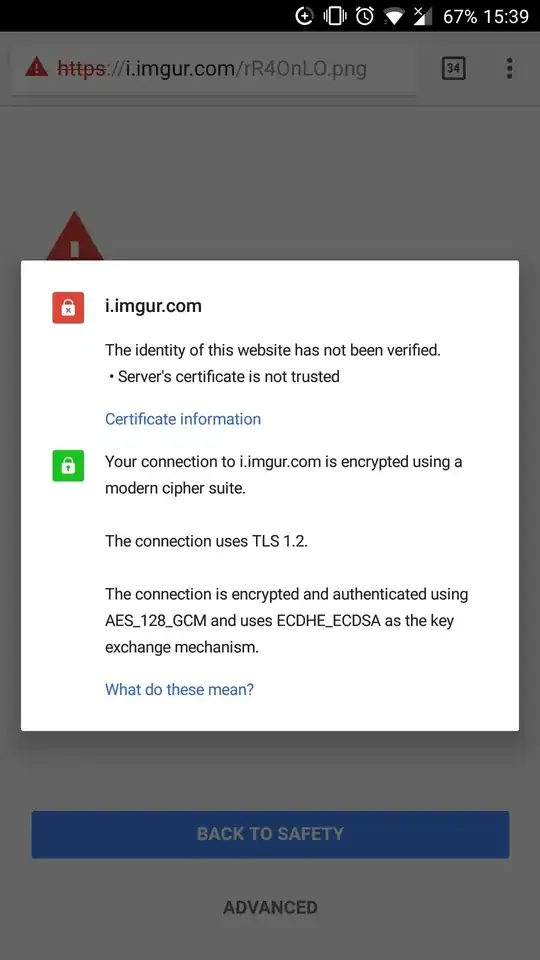
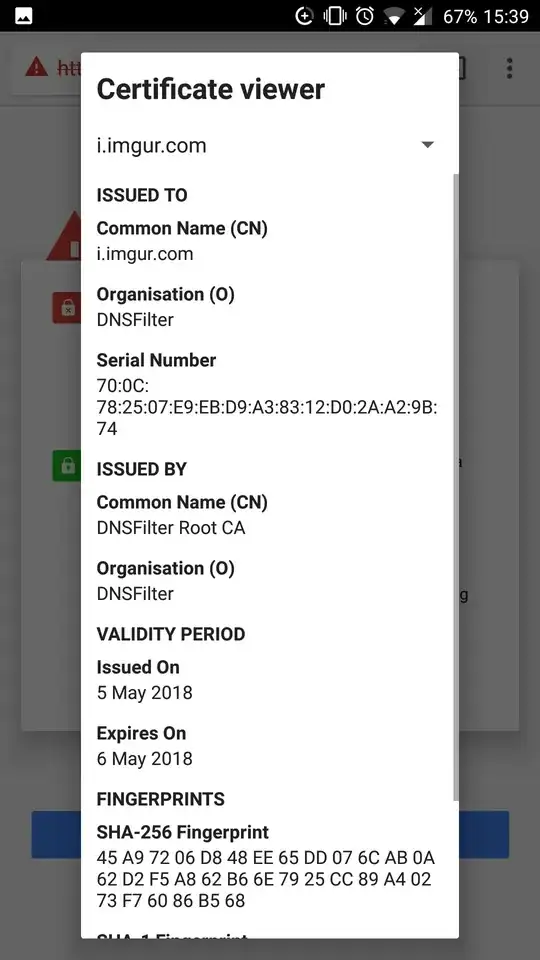
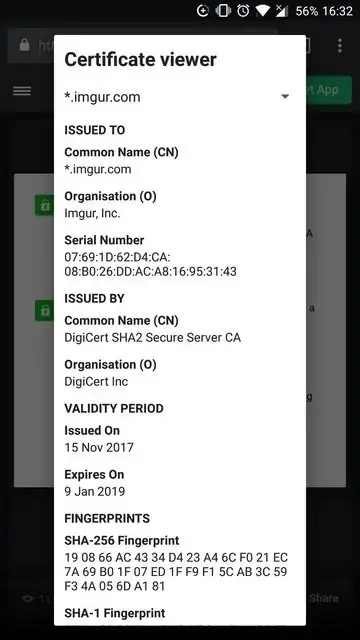
Is this certificate valid
No, it is generated on the fly by DNSFilter or an attacker pretending to be DNSFilter performing an MITM attack.
Why is this certificate being presented
DNSFilter allows monitoring network usage, and blocking sites, but when it blocks a site it wants to show an error message, so if the traffic is encrypted it needs to be able to decrypt it, which it can only do by either:
- Having the original certificate
- Making a new certificate
Why is there a warning
As the new certificate is not trusted by your machine you get a warning. This is true in both cases, an attacker CA would be untrusted, but so would the DNSFilter CA.
Why is the certificate only valid for a day
There are many reasons this could be, but a major one is trying to reduce the risk each individual certificate poses if it is leaked. The idea is that as long as the root cert is kept safe, then even if a site cert leaks, it is only trusted by devices that trust the CA.
As the certificates are generated on the fly there is no issue with the regular re-issuance that this requires.
Is SSL interception a good idea?
SSL interception is generally a very bad idea, for many reasons:
- Sensitive data may be logged by the intercepting device
- The keys may the same for all devices, so anyone can intercept with a copy of the master key
- The key may be gained from the device, leading to anyone being able to intercept
- EV certificates are downgraded to standard certificates
- Applications using pinning will not work with the changed certificate
There are some cases where it is acceptable, when absolutely necessary, but these do not apply for public WiFi, where you do not really trust the hotspot operator.