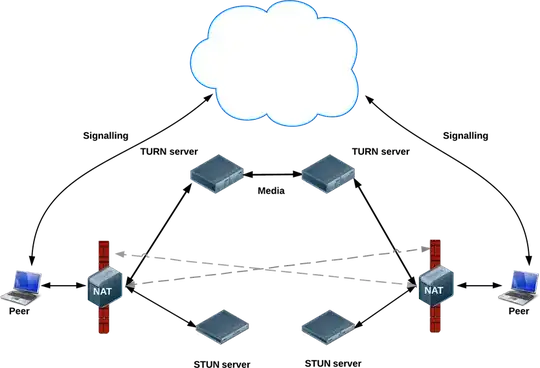
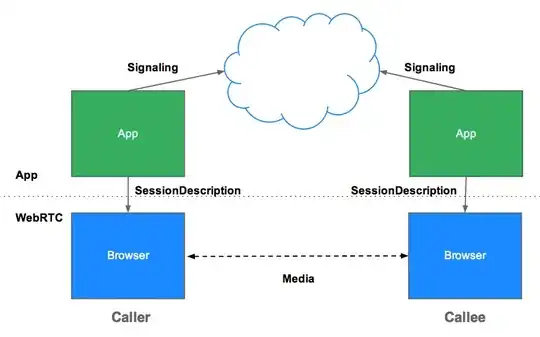
WebRTC makes use of TURN-Servers if the direct peer to peer connection fails. There are two protocols available: TURN and TURNS (TURN over TLS).
According to the MDN:
All data transferred using WebRTC is encrypted.
If all data sent via a data channel is end to end encrypted with DTLS by default, why does TURNS even exists?
Isn't TURNS only encrypting the connection between the server and the client?
Wouldn't that be unnecessary overhead?
EDIT - Why not simply use plain TURNwithout any server/client encryption? I know what TURN-servers are used for, but I do not get why we would want to encrypt the connection to the TURN-server. Because of the DTLS encryption between the peers, the TURN-server cannot read any of the transferred data. Hence nobody else can, so why even bother adding another layer of encryption?