In the Computer and network security incident taxonomy what are the differences between "Incident", "Attack" and "event"? Where does "threat" fit with them?
-
As always, have you looked any of this up? There is a lot of discussion around these terms. – schroeder Apr 22 '18 at 19:58
-
Just googled it. Nothing found in the context of taxonomy. – Mohammad Apr 22 '18 at 20:10
-
1Short version: Event - something happened. Incident - something suspicious happened. Attack - something is trying to harm us. Threat - that which tries to harm us. – Noir Apr 23 '18 at 08:57
-
2Attack: when it happens to my competitors. Event: when it happens to me! – Harper - Reinstate Monica Apr 23 '18 at 16:08
3 Answers
Assuming that you have looked up the official terms and wanted further help:
An event is something that has triggered notice. An event need not be an indication of wrongdoing. Someone successfully logging in is an event.
An incident is something that indicates a problem, however you define "problem". It carries from an event but has a layer of interpretation on top. Someone successfully logging in when they are on long-term sick leave and should be unable to use a computer is an incident.
An attack is an incident with malicious intent. Someone brute-forcing the credentials of someone on long-term sick leave is an attack. A manager asking the person on long-term sick leave for their password so that they can gain access to the person's work product for the benefit of the business is not an attack. It might be an incident, depending on your policies.
A threat is anything that has the potential to cause an incident. People, weather, machines, etc.
- 123,438
- 55
- 284
- 319
-
Just to be clear, So does that make an incident a threat? (Found that an incident is a warning that there may be a threat on security) – Mohammad Apr 22 '18 at 20:15
-
21As I say, threats cause incidents. Germs cause illness. Germs are not an illness. – schroeder Apr 22 '18 at 20:29
-
1As worded, it sounds like attacks are a subclass of incidents, and I'm not sure I agree with that. Plenty of attacks are utterly routine and should probably be considered non-incidents. Medical analogy would be that there's disease-causing bacteria all over your body and everything you touch, but it doesn't become a medical incident unless you actually get sick. – R.. GitHub STOP HELPING ICE Apr 23 '18 at 15:38
-
@mahmudKabir Example: An attacker who tries to guess passwords is a *threat*. But if you have proper password guidelines and your users follow them, they won't be successful. If the attacker is successful, you have an *incident*. Whenever you have an *incident*, then you will likely want to identify the *threat* which caused it so you can do the necessary *threat mitigation* to prevent this *threat* from causing similar *incidents* in the future. – Philipp Apr 23 '18 at 15:40
-
2@R.. not all attacks require incident response - thresholds for response are up to the organisation. Attacks still need to be tracked and monitored (and far more actively than waiting for bad things to happen). – schroeder Apr 23 '18 at 16:16
-
At least in ITIL, problem should probably be bolded. For example, someone logging in when they shouldn't is an incident. People *being able to* log in when they shouldn't would be a problem. Often, resolving the problem is much more involved than resolving the incident. – corsiKa Apr 23 '18 at 18:25
-
@Philipp An attack shouldn't need to be successful in order to be an attack. The fact that brute-forcing is possible is a threat, which can never be eliminated. Once someone's actually trying, it's an attack, regardless of its chance of success. – jpaugh Apr 23 '18 at 21:14
-
-
@corsiKa I don't thing schroeder was using the ITIL definition of "problem" and "incident". Security is not the main focus of ITIL. – Philipp Apr 23 '18 at 22:46
While schroeder's answer is certainly correct, it might not be formal enough. In the the terms and definitions of the ISO/IEC 27000 you will find the following:
threat
potential cause of an unwanted incident1, which can result in harm to a system or organization
information security event
identified occurrence of a system, service or network state indicating a possible breach of information security, policy or failure of controls, or a previously unknown situation that can be security relevant
information security incident
single or a series of unwanted or unexpected information security events that have a significant probability of compromising business operations and threatening information security
attack
attempt to destroy, expose, alter, disable, steal or gain unauthorized access to or make unauthorized use of an asset
An information security incident will always also be an information security event, but not all information security events will be information security incidents.
1: Not all incidents have to be information security incidents.
All quotes taken from: ISO/IEC 27000:2018: Information technology - Security techniques - Information security management systems
- 7,913
- 3
- 30
- 53
-
1Yes, there are numerous official, formal sources for these terms. I'm still unclear about what the OP is looking for, – schroeder Apr 22 '18 at 20:31
-
2In this definition, a log entry of a successful login, or a shutdown/reboot is not an event. However, many/most people might consider it an event. – MikeP Apr 22 '18 at 20:59
-
2@MikeP Well, a successful login or a reboot still indicate a **possible** breach of information security. It is only not a breach of security if the login was done by the authorized owner of the credentials and the reboot was issued by an authorized admin etc – Hagen von Eitzen Apr 23 '18 at 06:09
-
@MikeP As always the ISO norms gives whoever is setting up the ISMS of an organization more leeway than people might think. Hagen already pointed out the keyword "possible" in the definition of infosec event. If you set up your ISMS and say "I hereby do declare that from now on shutdowns, reboots and successful logins be information security events in this organization until I say they are no more." then that's absolutely fine. All you have to do is: to document it. – Tom K. Apr 23 '18 at 07:17
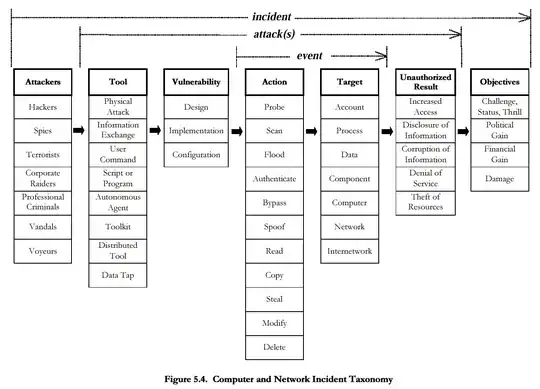
There are a lot of discussions up here and also talked with a professor of mine later on. However, in the taxonomy context following may help to understand the question,
Incident = (attacker) + ATTACK + (objective)
Attack = (tools) + (vulnerability) + EVENT + (unauthorized result)
Event = (action) + (target)
From the book "A Common Language for Computer Security Incidents" by John D. Howard and Thomas A. Longstaff following illustration would make the concept clear,
- 517
- 6
- 17
-
IMO what this chart misses is, that incidents and events can also be triggered by accident by employees or contractors. Being published in 1998 this paper is also somewhat outdated. – Tom K. Apr 24 '18 at 09:21
-
@TomK. As far as I can remember I first came to this chart into the security textbook of William Stalling last year. – Mohammad Apr 24 '18 at 09:43
-
-
@TomK. absolutely true. Perhaps that was not my point. My point was that this is still now in text curriculum. – Mohammad Apr 24 '18 at 11:08