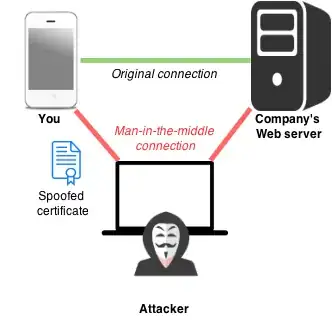
I just started to learn about MITM attacks, and I can't figure out few things. I have few questions and appreciate all the answers.
If the attacker is already in my LAN why does he need to trp to arp spoof or dhcp spoof, can he just sniff all the traffic on the network, or is it true only if there's a hub involved? if it isn't is it only in order to deal with the encryption?
why does the arp chart is able to change so quickly without any confirmation is there some kind of protection we can do?
I'm not expecting a full technical explaination of this but how does the attacker even gets into the network and gets to be part of the subnetwork? is that mean that he needs to hack into the router and make himself part of the lan? and does it means that he is part of 2 lans? one his and one the victims one?
Sorry in advance if some of the questions are vogue or weird , just trying to understand.