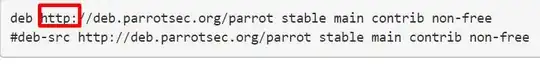
The packages in Debian-based distributions are cryptographically signed, tampering with them would be very difficult. (In fact, they typically use the same algorithm that is used to authenticate a server over HTTPS.) Sending packages over HTTP has a number of advantages:
- Intermediate proxies can cache the packages. (I run a local
apt-cacher-ng instance for exactly this reason.)
- There is less load on the mirror servers.
- There is no need to manage the TLS certificates for the mirrors. (Consider that a single hostname might resolve to multiple mirrors run by different organizations, such as universities, companies, private individuals, the distribution itself.)
There is a lack of confidentiality, but the integrity of the packages should remain so long as OpenPGP is considered secure. Note that even with TLS, it is likely to be trivial to identify the packages you are downloading from a mirror.
You've identified Kali and Parrot as "security distributions", which is a reasonable classification, but it's probably worth noting that they are designed for the use of security tools, not for being a secure platform themselves. You need look no further than Kali's "root by default" policy to see that ease of use of tools has outweighed security of the distribution in their balance. If you're using Kali because you think it gives you a secure desktop, you should reconsider.