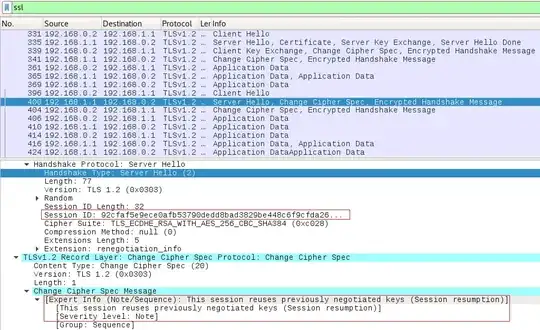
I made a Wireshark tap for 2 request:
- a HTTP GET to a login authentication page
- then a HTTP POST when I send credentials to the server
As you can see, I get a warning message from Wireshark because it seems that the TLS session ID is the same for both "Server Hello" packet number 335 and packet number 400.
Is that normal behaviour?