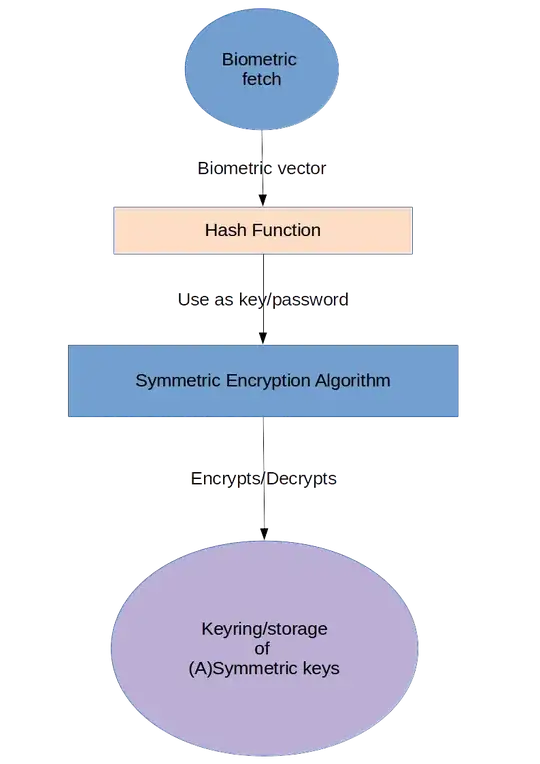
As I was studying a paper authored by Anna Romanou with title "The necessity of the implementation of Privacy by Design in sectors where data protection concerns arise" I came across Ann Cavoukian's proposal that states on how to use biometrics.
What is stated is to use biometric characteristics as a key to encrypt another credential such as pin, password, conventional cryptographic keys and using the second type of credential as authentication, therefore there is no need to store biometric information that is extremely sensitive.
So if a software/systems Engineer wanted to use this type of cryptography, what algorithms/libraries does he/she has at his disposal?
Note: The purpose of this question is to create a public index of libraries and algorithms for these type of encryption in order for our colleagues to use it. For example, a .NET developer can use the X library.