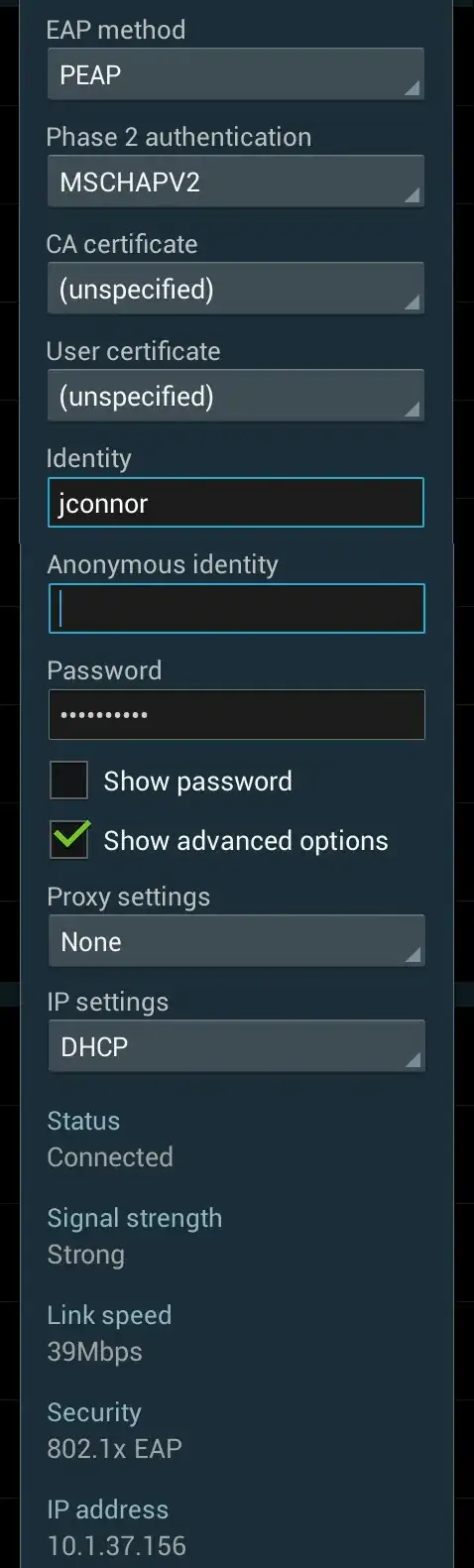
Is it possible for an 802.1x network (PEAP/MSCHAPv2) to have no certificate (CA, user, or otherwise)?
PEAP/MSCHAPv2 doesn't typically use client certificates, nor does it directly use any CA certificates in establishing a TLS connection (*see below). However it certainly requires the use of a server certificate (PEAP is a TLS tunneled EAP protocol).
If so, what are the security implications?
The image you provided indicates you are likely using some form of *nix which is giving you two certificate options.
Addressing the second option (client certificate) first, the vast majority of users connecting to wireless with a network using PEAP/MSCHAPv2 will never need this field (I have configured/deployed thousands of APs in numerous environments and have never seen this used personally).
The important option is the first one, the CA certificate field. Why? Because this helps to significantly reduce the possibility of connecting to a fake or rogue wireless network trying to impersonate the one to which you intend to connect.
This begs the question of how the CA certificate helps. Keep in mind that before successful authentication to the network, your client has no access to the network or the resources on it. The AP or wireless controller acting as the NAS (network access server) is proxying the connection from your client devices EAP supplicant to the RADIUS authentication server. The CA certificate is being used to help validate the identity of the RADIUS authentication server to which your EAP supplicant is authenticating.
Generally speaking, the EAP supplicant must make a decision on whether it will send your username/password to the authentication server without being connected to the network. This means it is only able to work with information it has and information it is given by the authentication server, it can't go out on the Internet to check another source until after it has authenticated and it is too late to withhold your username/password.
The EAP supplicant does this primarily by checking two things (with a couple options present in many EAP supplicants like Windows and OSX, but often not on mobile devices like tablets and phones):
- Is the certificate provided by the authentication server a valid certificate issued from a CA trusted by the client device?
- (Optional) Is the certificate issued from the designated CA(s) in the EAP supplicant?
- Does the hostname listed on the certificate match the hostname given by the authentication server?
- (Optional) Is the hostname given by the authentication server one of the hostnames allowed in the configuration of the EAP supplicant?
The other options for the EAP supplicant are to either have the OS prompt the user to "check and approve" the certificate (bad idea) or to not validate the certificate at all (worse idea) before sending your username/password.
So providing the CA certificate in your EAP supplicant configuration will help by allowing it to use #2 above to validate the identity of the RADIUS server in addition to #1 and #3. You should be able to get the correct CA information and/or certificate from your IT department.
Note: portions of this answer were copied from another of my answers.