OAuth2 is not intrinscally a security risk for an end-user, i.e. the person authenticating on a third-party service using their Google or Facebook account (for example).
OAuth2 works in scopes, which define the nature and amount of data the third-party service will end up having access to.
You will probably be familiar with this kind of screen (source):
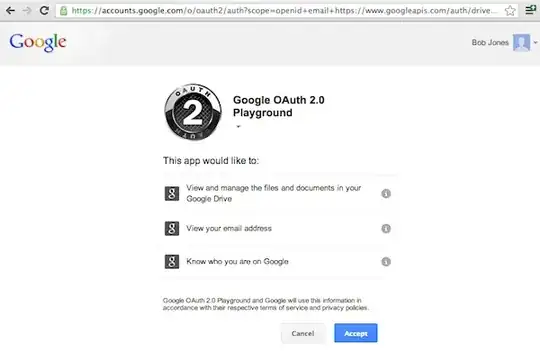
A well-designed OAuth2 implementation will clearly express the various bits of information that will be disclosed to the third-party service.
However, this really depends on the OAuth2 provider's apt definition of scopes. There are no standard scopes, so they vary from provider to provider, as shown in this scopes-by-provider list.
Therefore the "outside risk" lies in your choice of OAuth2 provider. It is possible to implement OAuth2 in a totally insecure way, and still "adhere" to the OAuth2 specification. What if I ran a service with a single scope for all your information? What if my description of such scope in the consent page was misleading?
More generally, it is often a criticism of the OAuth2 specification that it leaves critical elements out for the implementers to make up by themselves, leading to all sorts of problems. The wikipedia page briefly brushes on them (please feel free to go down the rabbit hole and read up on it).
But this does not make OAuth2 itself intrinsically insecure.
Addressing the current Cambridge Analytica scandal: Facebook, for all that could be held against them, run a reputable OAuth2 implementation and have been providing this service for years before this event. People who surrendered their information in the Cambridge Analytica debacle must have initially clicked through the consent screen, which must have displayed an item about disclosing their friends circle, when using the psychological profiling app that ended up fishing (not phishing) for all this information. It seems however, that Facebook has at least been "negligent" in enforcing its data usage policy (make up your own mind).
Edit: @Ian commented that the Cambridge Analytica’s app users may not have given explicit consent for their friends data to be pulled. I suppose it means Facebook may not have been straightforward in the description of their scope.
As for your last question, an OAuth2 provider is not able to tell any more than when and how often the third-party service accesses the scoped information. It cannot know what you are doing with the third-party service, or for that matter, what the service is doing with your information. It's (rightly) out of their hands.
