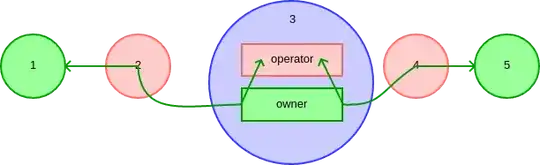
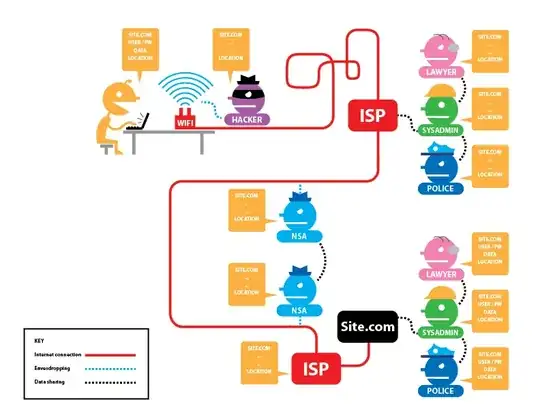
If I'm communicating security and trust over a network, I might simply note trusted and untrusted nodes. For example, when making an HTTPS connection over some kind proxy node that I own and operate, I trust the protocol and the entire node:
But some connections are more nuanced. I can trust HTTPS to secure the content of my message and the identity of the destination, but activity logs depend on my relationship with the operator and owner of the node. I might operate the node but not own it. Or own it but not operate it. Or neither.
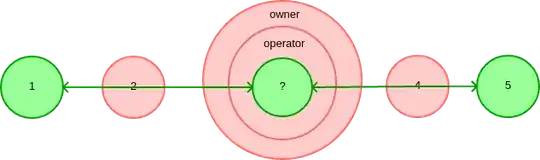
Failed attempt 1
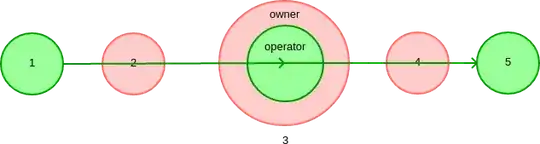
Failed attempt 2
How can I diagram this? (A general notation for layered trust on a single node is welcome. In other words, not specific to HTTPS and proxying.)