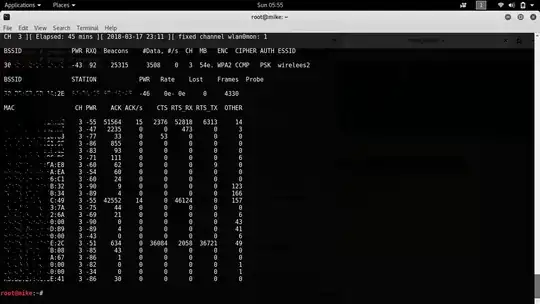
What are the extra MACs in airodump display that are not real associated adapters? What are they for? There are only 4 things connected to this router - (verified by viewing router dhcp list) but there are over 15 MACs displayed by airodump-ng. I see the actual MACs have higher ACK times.
Asked
Active
Viewed 1,245 times
3
-
2Associated stations of other access points in your neighbour listening on the same channel on which you are. Use this to only capture your stations `airodump-ng -c 9 --bssid 00:14:6C:7E:40:80 -w psk wlan0mon` – defalt Mar 18 '18 at 12:38
-
some reason when i use channel switch -c airodump still displays "fixed channel wlan0mon:...." appears to still scan thru channels 1-12 - and your explanation verifies it is indeed still scanning and listing other access points.....likely why im having trouble capturing handskake.....i will try "airmon-ng start wlan0 3" to see if that locks channel to adapter - TY for info & logical lead – learning2 Mar 18 '18 at 12:57
-
What makes you believe they're anything other than client devices (cell phones for example) looking for WiFi? – Nomad Apr 18 '18 at 22:42
-
Have you activated option `-a` ("Filter unassociated clients")? – Faither Jun 13 '22 at 06:16
1 Answers
1
not sure how public we are trying to make the solutions, but figure this will be a buried question soon anyway once answered....but i greatly appreciate the help given and found and would like to return favor only way i know.
try change attacker MAC to same as victim router MAC then begin attack https://security.stackexchange.com/a/72538 (related to problems w/deauth) (1)So do this:
Disable mon0.
Shut down wireless interface ifconfig wlan0 down (or whatever your interface is called).
(my step) run: airmon-ng check -> kill NetworkManager PID (networkmanager fucks up hw ether mac change)
Set the attacker's MAC to your routers: ifconfig wlan0 hw ether TARGET_MAC.
(this is where u do the monitor mode method)Reactivate interface, create new mon0 and do your deauth attack. It should work now. (Also make sure replay the deauth packet 3-4 times as for some reason sometimes a single death just won't work.)
(3)try When you enter monitor mode you can specify a channel like this: "airmon-ng start wlan0 x" where x is the channel number
(2)try alternative monitor mode method: https://security.stackexchange.com/a/135841
ifconfig wlan0 down
sudo iwconfig wlan0 mode monitor
sudo ifconfig wlan0 up
This is can cause SIOCSIFHWADDR: Invalid argument error
iwconfig wlan0 mode managed (to undo monitor mode & fix error)
learning2
- 41
- 3