I went online on my Macbook today and noticed my iTunes complaining that it couldn't connect to Apple, I tried logging out and in of my account but weirdly it said it couldn't log in; I didn't think much of it at first as I thought maybe it was iTunes just being more buggy than usual.
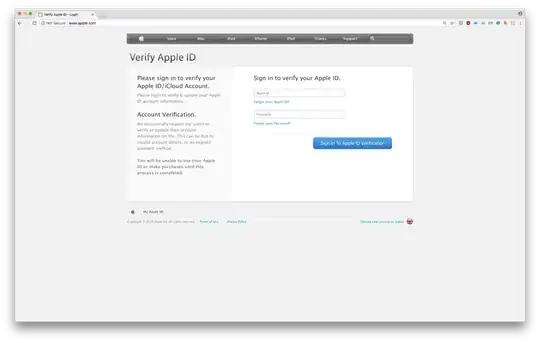
However then I noticed something really weird, when I tried to visit www.apple.com my browser warned me (Google Chrome) saying this website was not secure. This started ringing alarm bells in my mind, I clicked "Continue Anyway" and was greeted with this page:
Being (somewhat of) a web designer/developer I pay attention to the little details on a website and I knew instantly this was not what the Apple homepage looks like, and they certainly didn't prompt you to login on their homepage. I dug in a little deeper to the source code for the page and could see that the source code was way too simplified for a large corporation; the only piece of JS was to verify that the email address was in the right format.
I began to suspect maybe my Mac machine had been infected, so I switched to my iPhone (on the same WiFi network), tried www.apple.com, and got shown the exact same page. To me this sounded like something to do with DNS as the chances that both my devices were infected were very unlikely. I then turned to my router to have a look at its settings.
Lo and behold, when digging into the DNS settings I could see that the settings looked a little odd. I had initially set my DNS settings to use Google's servers, although this was set many years ago I knew the were something along the lines of 8.8.*.*.
In my settings however I found the following IP's:
Primary: 185.183.96.174
Secondary: 8.8.8.8
I knew straight away that the DNS had been changed, the primary address should have been 8.8.4.4. No one has access to my router administration page aside from me on the network, and I have disabled access to the router outside of the local network I can see outside access was enabled, on initial setup this was definitely switched off.
My question is: "How could the DNS have been changed/What can I do to prevent this from happening again?
I try to keep my router firmware up to date (although I was maybe 1 release behind at the time of this post).
More about the phishing site:
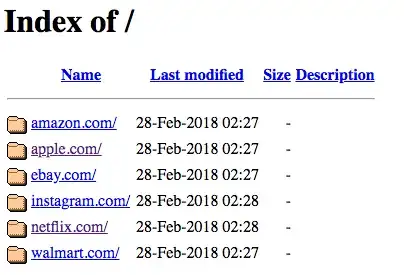
Before I changed the Primary DNS setting back and I wanted to find out more about this phishing site, so I ran ping apple.com to find the IP address was 185.82.200.152.
When I entered this into a browser I could see that the person had created a number of sites to try and capture logins. I suspect they're based in the US; I don't believe Walmart operates outside of the states (at least not in the UK). I have reported the IP to the Dubai based web host and am waiting for a response.
Edit (Router details):
Asus AC87U, FW Version 3.0.0.4.380.7743 (1 release behind)
I did not have the default passwords set.
Second update:
Host has suspended the account.