By default, mitmproxy will use its own local IP address for its server-side connections. What I want instead is mitmproxy to use the client’s IP address for server-side connections.
The following config is supplied to make this work:
CLIENT_NET=192.168.1.0/24
TABLE_ID=100
MARK=1
echo "$TABLE_ID mitmproxy" >> /etc/iproute2/rt_tables
iptables -t mangle -A PREROUTING -d $CLIENT_NET -j MARK --set-mark $MARK
iptables -t nat \
-A PREROUTING -p tcp -s $CLIENT_NET \
--match multiport --dports 80,443 -j \
REDIRECT --to-port 8080
ip rule add fwmark $MARK lookup $TABLE_ID
ip route add local $CLIENT_NET dev lo table $TABLE_ID
Mitmproxy is listening on the router (192.168.178.40) on port: 8080
However, my setup consists of a custom Debian router with 2 NICs.
- One internet-facing
wlp2s0(also used to SSH into it) with address:192.168.178.40 - One NIC set as default gateway
enp4s0for the target client at:10.0.0.1
The client connects to the default gateway with the address 10.0.0.12
By default I use the following IP table rules to redirect my client traffic to port 8080:
sudo iptables -t nat -A PREROUTING -i enp4s0 -p tcp --dport 80 -j REDIRECT --to-port 8080
sudo iptables -t nat -A PREROUTING -i enp4s0 -p tcp --dport 443 -j REDIRECT --to-port 8008
While this works as intended, I'd like to be able to spoof the client source address so that the HTTP(S) requests captured match the TCP packets and other traffic also coming from the client.
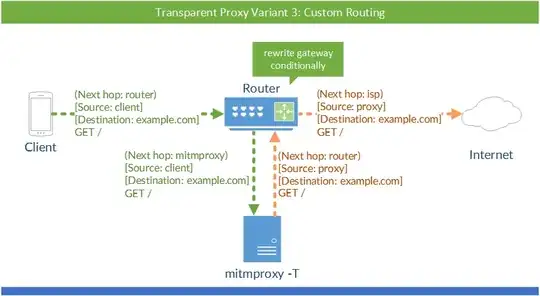
Here's a picture to visualize my setup because I am pretty horrible at explaining: