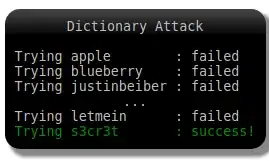
I am curious about password cracking methods like dictionary and brute force attacks. Nowadays passwords are stored as hashes and not plaintext on the server. Then how can the plaintext passwords in the dictionary be compared with the hashes in the leaked database? Since the hashes can be of different types like bcrypt, SHA-512 and so on, how can the cracking tools know how to create the hashes and compare it?
For example, take a look at the dictionary attack below. The leaked passwords are just hashes and the dictionary has simple English words. Then how can they be compared? How does the attacker or the cracking tools know what hash algorithm it should use? Even the salt is there, but how does the attacker know what the salt is?